Data Protection in Healthcare: A Comprehensive Guide
Every organization handling healthcare data operates with a target on its back. Cyber threats and insider risks have turned protected health information (PHI) into one of the most valuable commodities on the black market.
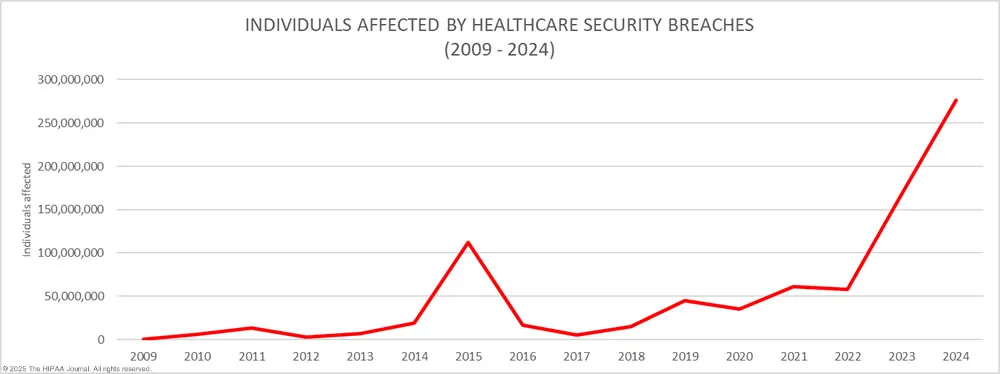
Between 2009 and 2024, the US experienced nearly 6,800 healthcare data breaches, each involving a minimum of 500 records. The 2024 cyberattack on Change Healthcare exposed the personal data of over 190 million people – more than half the US population. That’s an astonishing number. The cost to UnitedHealth? $2.3 billion and counting, roughly $1 billion more than previous estimates.
The cost of a single breach can cripple an organization. But protecting sensitive data goes beyond compliance or avoiding fines; it’s about safeguarding trust, ensuring continuity, and staying ahead of relentless threats.
The question is no longer if an attack will happen but when, and the time to implement proactive data protection strategies is now.
Read on to learn about the importance of securing patient information. We’ll also cover common threats to healthcare data and provide proven strategies to protect PHI.
How GoodRx Protects Billions of Sensitive Records with Skyflow. Watch now →
The Importance of Data Protection in Healthcare
When a ransomware attack paralyzed Change Healthcare in early 2024, it disrupted operations and sent shockwaves through the entire healthcare system. More than half of Americans may now have their personal health data exposed.
This was not an isolated event. It was a warning shot.
Healthcare data breaches are no longer rare or random. They're systemic, frequent, and devastating – financially, operationally, and reputationally. Every breach puts lives, trust, and care at risk. And with public visibility at an all-time high, the damage extends far beyond internal systems.
The time to act isn’t after a breach. It’s now.
Here’s why data protection must be a top priority for every healthcare organization:
Protect against rising cyber threats
Healthcare data is under attack at an ever-increasing rate.
The HHS Office for Civil Rights (OCR) has reported a 256% increase in large data breaches involving hacking over the past five years. In 2023, hacking accounted for 79% of the large breaches reported to OCR, affecting over 134 million individuals – up 141% from 2022.
And then came 2024.
The Change Healthcare breach alone impacted over 190 million individuals, contributing to a year where more than 250 million people’s data was exposed across the country.
Healthcare organizations are no longer just targets – they’re easy targets. Holding electronic health records, financial information, and sensitive patient data makes them incredibly valuable to attackers. And once hit, recovery is costly, complex, and highly visible.
Maintain patient trust and organizational reputation
Trust is the foundation of healthcare. When patients share personal health information, they expect it to stay private. A breach shatters that trust in seconds.
Patients who fear their data isn’t safe may withhold critical information or seek care elsewhere. Worse, public outrage and media coverage can cause long-term damage to a provider’s reputation. Take 23andMe, a company that offers genetic reports from saliva swabs.
The company peaked at $6 billion in market value in 2021. However, its reputation took a massive hit following a breach in 2023 that exposed the data of 6.9 million customers, including those specifically with Ashkenazi Jewish and Chinese backgrounds. 23andMe settled for $30 million but the damage was done. Privacy concerns amidst the devastating breach are credited as one of the reasons why 23andMe ended up filing bankruptcy.
When breaches make headlines, the harm can go viral. This public visibility highlights the importance of maintaining strong data protection practices to safeguard patient trust and organizational reputation.
Securing protected health information (PHI) protects the trust that allows healthcare to function. It keeps patients engaged, reputations intact, and care on track.
Meet regulatory compliance requirements
Compliance is a guardrail that keeps organizations from falling into legal and financial ruin. Healthcare providers must comply with regulations like:
- The Health Insurance Portability and Accountability Act (HIPAA) establishes regulatory standards for protecting PHI. Organizations must implement the appropriate safeguards to prevent the unauthorized use or disclosure of medical data.
- The Health Information Technology for Economic and Clinical Health Act (HITECH) strengthens HIPAA compliance requirements and expands its scope to businesses that process healthcare data.
Then, there are state-specific laws like the California Consumer Privacy Act (CCPA) and international regulations like the General Data Protection Regulation (GDPR), which have additional data protection requirements.
Failure to comply can cost millions. For example, Cignet Health was fined $4.3 million for violating the HIPAA Privacy Rule by denying patients access to their medical records.
Regulations are only getting stricter. The cost of falling behind – both financially and reputationally – continues to climb.
How GoodRx Protects Billions of Sensitive Records with Skyflow. Watch now →
Challenges and threats to protecting healthcare data
The sensitive nature of PHI makes it a high-value target. Individual healthcare records can fetch up to $250 on the dark web, 50x more than payment card details.
It’s not just cybercriminals and bad actors. Insider risks, outdated systems, regulatory gaps, and even the rise of AI all expose organizations to breaches.
Without a clear understanding of these threats, healthcare providers risk falling behind. Strong protection starts with knowing where vulnerabilities lie.
Ransomware attacks
Ransomware is one of the most damaging threats in healthcare today. And it’s accelerating. In 2024, 67% of healthcare organizations were hit, up from 60% in 2023.
Some attacks now use “double extortion,” which involves stealing and encrypting data. This forces healthcare organizations to pay ransoms to decrypt their data and prevent its release. Organizations affected by ransomware paid an average of $4.4 million.
Mitigation strategies:
- Segment networks to contain malware spread
- Create and regularly test ransomware incident response plans
Insider threats
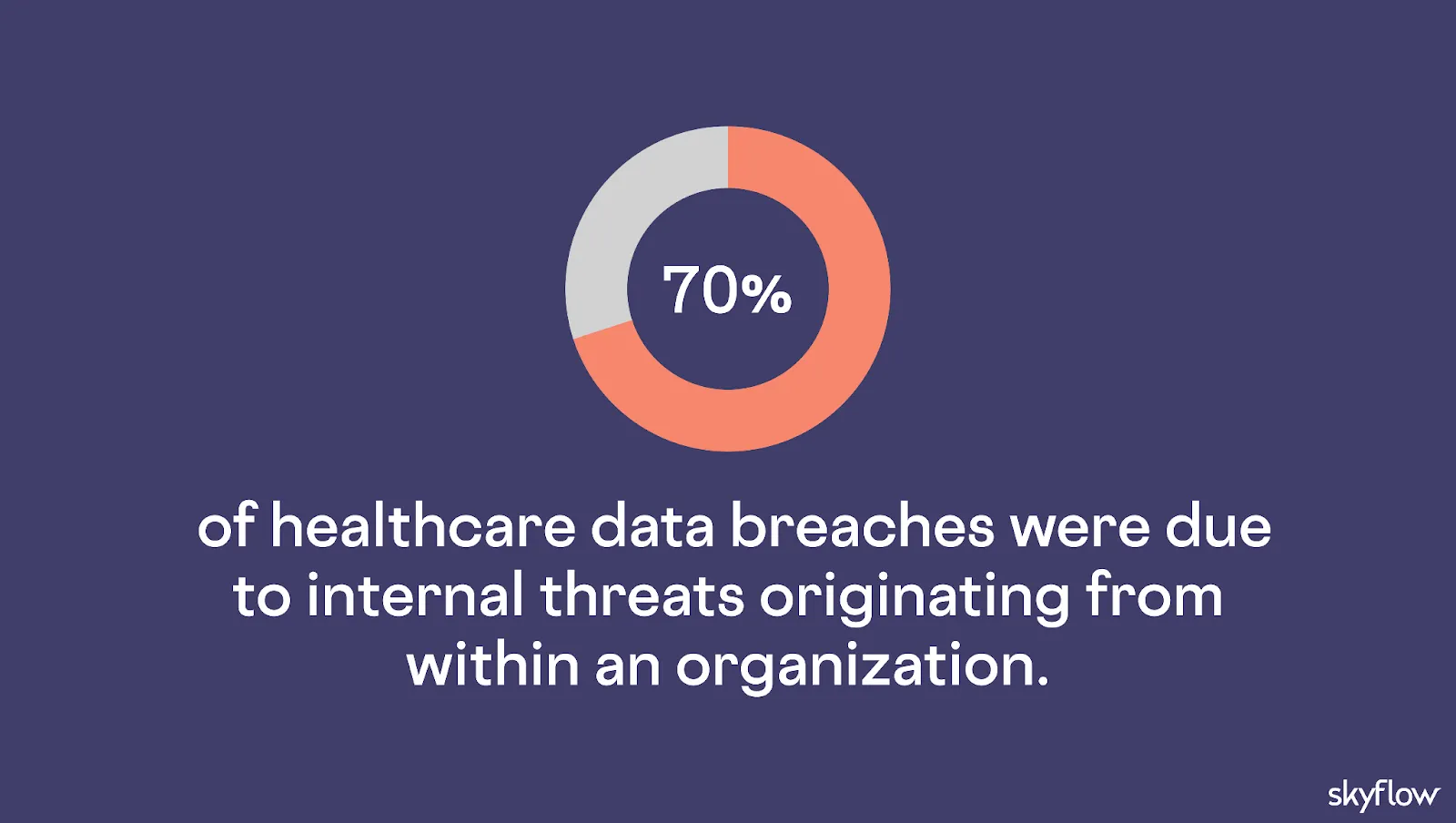
Not all threats come from outside. Insider threats, whether intentional or accidental, accounted for 70% of healthcare data breaches, according to a report from Verizon.
Malicious insiders intentionally misuse their access for personal gain or out of curiosity – like the clinic worker who received a five-year jail sentence for stealing and selling PHI.
Negligent insiders unintentionally expose sensitive data due to carelessness or failure to follow proper protocols. For example, HealthReach Community Health Centers discovered a worker at a data storage facility improperly disposed of hard drives containing PHI.
Most incidents stem from privilege misuse or miscellaneous errors, and most can be prevented with the right safeguards.
Mitigation strategies:
- Train staff to recognize phishing attempts
- Enforce strict access controls to limit unnecessary access
Technical infrastructure complexity
Healthcare data lives across dozens of systems, which make it difficult to secure sensitive data. This is known as “sensitive data sprawl,” which occurs when data replicates across systems. Every location where data is stored becomes a potential target for cybercriminals, greatly increasing the risk of a breach.
Here’s an example of an architecture with sensitive data sprawl:
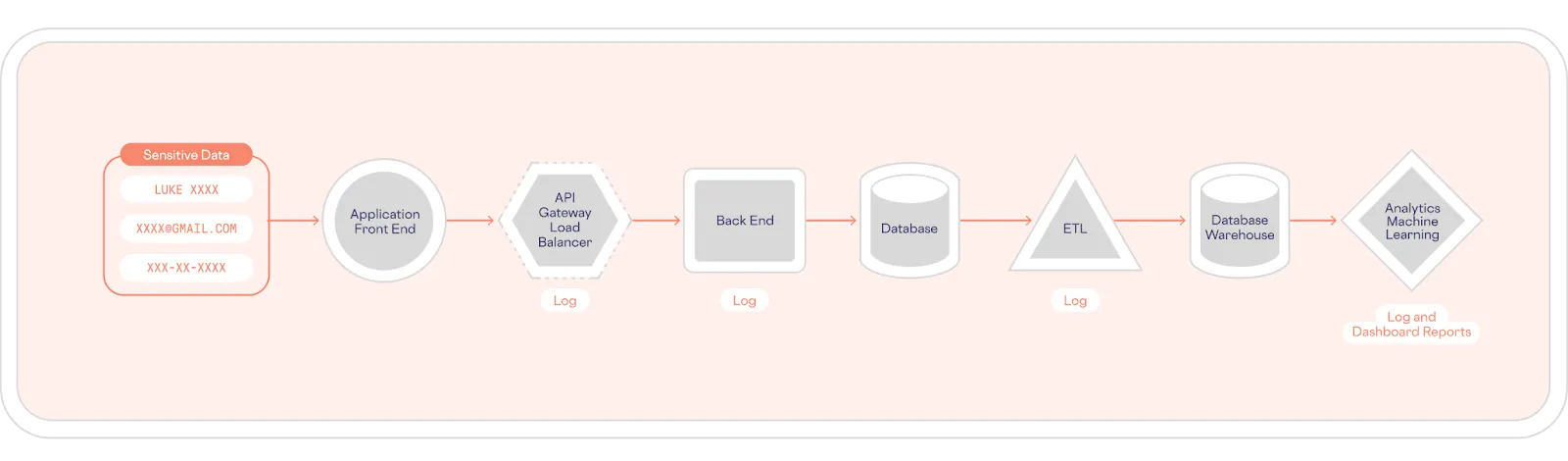
Outdated legacy systems compound the risk of securing healthcare data. Many lack basic protection like encryption and may no longer receive updates and patches to fix vulnerabilities. Yet replacing them isn’t easy. Modernization may disrupt operations and impact patient care.
It’s a balancing act, and one health system execs know well: upgrading legacy systems is their second biggest digital transformation challenge, just behind budget constraints.
Mitigation strategies:
- Adopt a zero-trust architecture to limit lateral movement
- Use compensating controls like multi-factor authentication (MFA) where upgrades aren’t yet possible
Regulatory compliance requirements
Healthcare privacy laws are evolving fast, and falling behind comes at a cost.
Providers located in the US must comply with key regulations like HIPAA, CCPA, and PCI-DSS. The FTC has also finalized new changes to the Health Breach Notification Rule, which now also applies to health-related applications not covered by HIPAA.
But staying compliant is challenging. Penalties for HIPAA violations alone range from $141 to over $2,1 million, depending on the severity of a breach and the level of negligence.
Mitigation strategies:
- Review HIPAA requirements and implement the appropriate safeguards
- Designate a HIPAA compliance officer to manage ongoing compliance efforts
Use of AI
AI is becoming ubiquitous in healthcare. 81% of healthcare cybersecurity professionals report their organization allows the use of AI. Alarmingly, 30% say it’s used without formal restrictions.
The risk?
AI tools don’t have a “delete” button. Much like sharing something online, once PHI is fed into an LLM, there’s no mechanism to “unlearn” it. In some cases, prompt injections can even surface sensitive data unintentionally (e.g., “Show me medical records on X”).
Without clear policies, well-meaning healthcare professionals could expose confidential information without realizing it.
Mitigation strategies:
- Enforce strict policies around the use of AI tools
- De-identify all healthcare data before using it with AI
Staying ahead of the threats demands action, building a security framework that can withstand today’s risks and preparing for tomorrow’s.
Data security in healthcare: Solutions and best practices
Cyberattacks, insider threats, and regulatory risks are escalating. To stay secure and compliant, organizations must take action with proven, proactive measures that protect data wherever it lives and however it’s used.
Here are seven best practices healthcare organizations can adopt to secure sensitive healthcare data, maintain patient trust, and meet regulatory obligations:
1. Review HIPAA and GDPR requirements
Healthcare organizations must comply with a growing number of regulations. In the US, HIPAA lays out three rules for protecting PHI:
- Privacy Rule: Prevents unauthorized use or disclosure of PHI and gives patients the right to access their records.
- Security Rule: Requires covered entities and business associates to implement physical, technical, and administrative safeguards to protect PHI.
- Breach Notification Rule: Mandates healthcare organizations notify affected individuals within 60 days of a breach of their data.
GDPR has a broader scope, as it applies to all personal data related to EU/UK residents. Healthcare data falls under a “special category,” which requires additional steps, such as obtaining explicit consent and data minimization.
Don’t stop at HIPAA and GDPR. Regulations like PCI DSS 4.0 may also apply. Staying informed is critical to staying compliant.
2. Isolate healthcare data with a data privacy vault
Data sprawl remains one of the biggest threats to healthcare data security. One effective method to address sprawl is with a data privacy vault, which secures and protects PHI.
By isolating PHI and other critical data, healthcare organizations can reduce their attack surface, simplify compliance efforts, and create a “single source of truth” that’s easier to manage and protect.
Here’s an example of a data privacy vault that isolates, protects, and governs access to sensitive data:
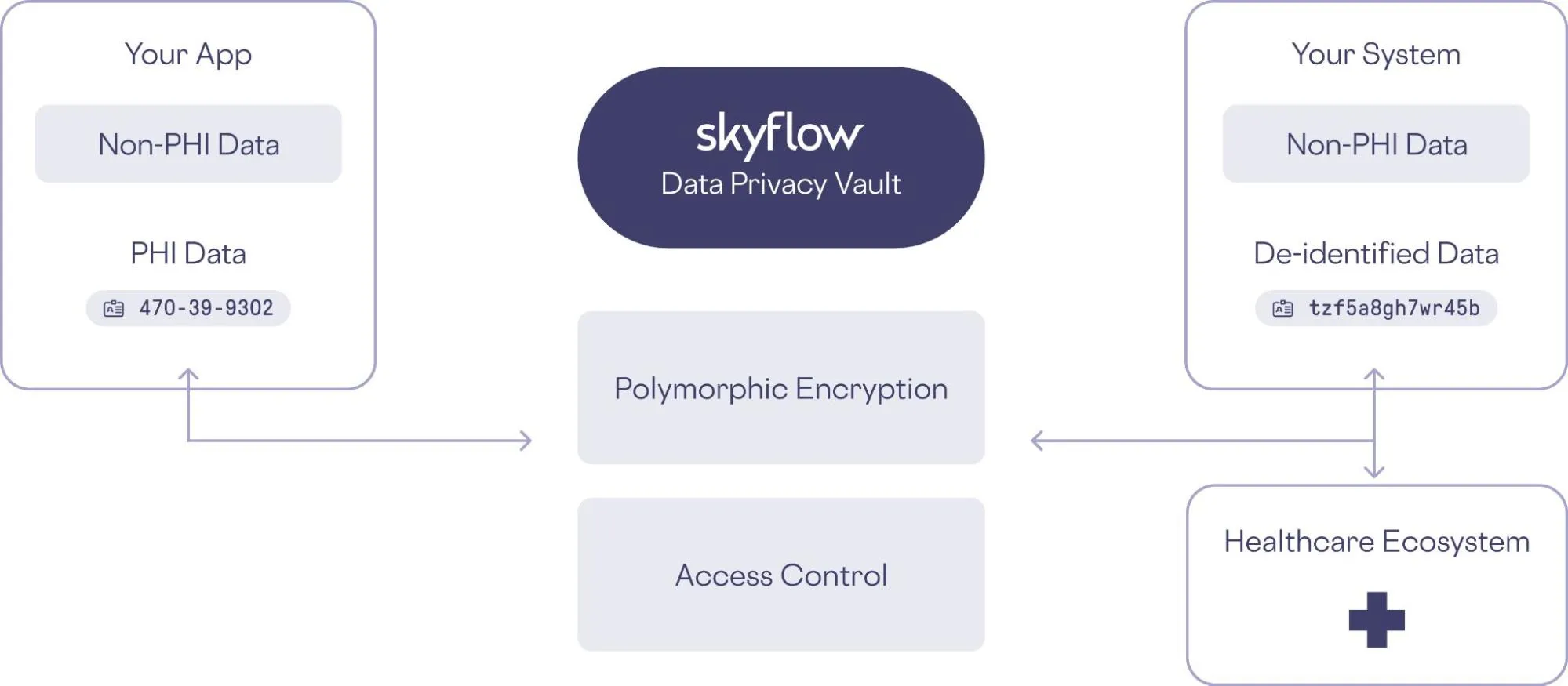
Compliance management is also simplified since sensitive data is properly isolated, protected, and governed. There is only one place to apply changes, so staying ahead of evolving regulatory landscapes is easy.
With the risk of breaches reduced, so are the associated legal penalties. Healthcare providers can maintain trust between patients and protect their reputations.
Once sensitive data is isolated, organizations can dramatically lower the chances of unauthorized access by implementing advanced techniques like polymorphic tokenization.
3. Use tokenization to obfuscate sensitive health data
Even with secure storage, data needs protection at the element level. That’s where tokenization comes in.
Tokenization replaces sensitive data with non-exploitable tokens. It “insulates” infrastructures from exposure and reduces compliance scope.
Format-preserving tokenization preserves the format of the original value while making it unreadable to unauthorized users.
Here’s an example of format-preserving tokenization:
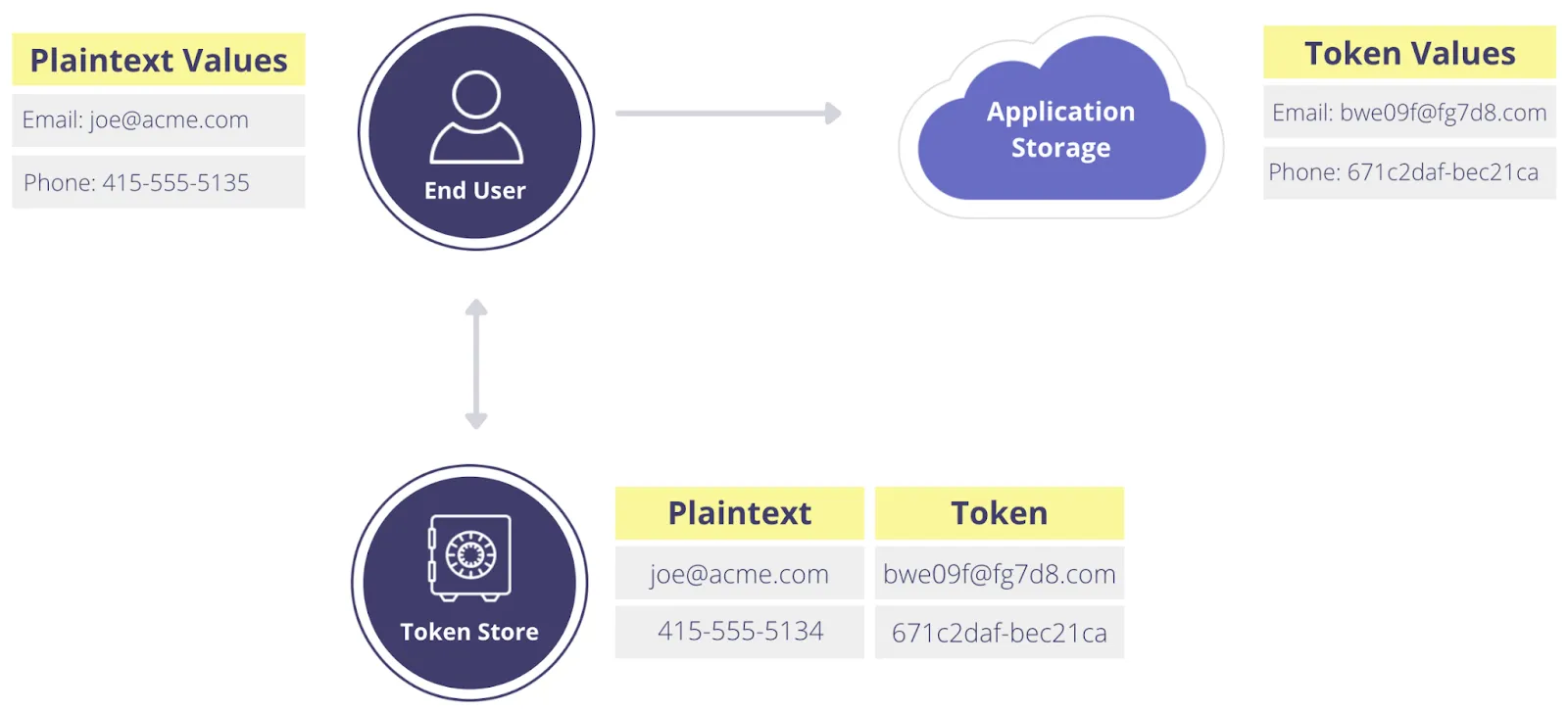
Even if a data store containing tokenized data is breached, tokenized data is useless without access to the tokenization process. When paired with a data privacy vault, organizations can map original values securely – and add additional protection through redaction or masking.
4. Implement fine-grained access controls
Snooping on patient records is one of the most common HIPAA violations. For example, a Washington hospital was fined $240,000 after it was discovered that security guards had accessed medical records without a valid reason.
Fine-grained access control helps healthcare organizations manage and restrict data access based on user roles. Implementing strict access controls at the data layer protects sensitive data from external threats and mitigates internal risks by consistently enforcing the least-privileged data governance policies. For instance, doctors should only be able to see their own patients’ data – not every record in the system.
Implementing role-based access control (RBAC) and regularly reviewing user access helps mitigate both internal and external threats.
5. Require MFA on critical systems
During the Change Healthcare cyberattack, attackers used stolen login credentials to access a server that lacked MFA. From there, they gained entry into UnitedHealth’s network. Requiring MFA on all key systems could have prevented this breach.
Requiring MFA across all critical systems significantly reduces the risk of unauthorized access. Start by identifying all systems that store or process sensitive healthcare data and ensuring MFA is enforced – ideally using app-based or hardware token methods rather than less secure SMS-based authentication, which is vulnerable to SIM swapping attacks.
6. Develop and implement an incident response plan
Even with strong security protocols, data breaches can still happen. That’s why a well-defined incident response plan is essential for restoring operations quickly and minimizing damage.
However, only 42.7% of companies have an incident response plan and test it at least once a year.
To be effective, your plan should clearly define roles and responsibilities, include “playbooks” for different types of attacks, and be supported by regular risk assessments and tabletop exercises. Some organizations also consider cyber liability insurance to protect against financial losses in the event of a breach.
7. Provide training to raise security awareness
A phishing attack on Atrium Health compromised the personal data of over 32,000 patients. Incidents like this highlight the critical role that employee awareness plays in data security.
Comprehensive security awareness training equips healthcare staff with the knowledge to recognize and respond to threats like phishing, social engineering, and weak password practices. It should also include procedures for reporting suspicious activity or incidents.
Ongoing education and reinforcement are essential to building a culture of security that extends beyond technical controls.
Real-world use cases: GoodRx
An example of successful implementation is the collaboration between GoodRx and Skyflow. GoodRx faced the challenge of keeping records from 240 million patients safe from potential threats while ensuring that internal access to data was tightly controlled. They initially attempted to build and maintain a data privacy vault internally but encountered security issues that made this approach unsustainable.
By migrating 710+ million tokens to Skyflow’s platform in less than three weeks, GoodRx minimized architectural changes and operational impact. This transition allowed their engineering team to focus on enhancing customer experiences, reduced the total cost of ownership by 67%, and significantly increased data privacy standards. With Skyflow, GoodRx can also ensure privacy for LLMs and analytics, a capability that was not previously possible.
To learn more about how Skyflow helps GoodRx better protect healthcare data, you can watch this talk given by Skyflow’s CEO, Anshu Sharma, and GoodRx’s CTO, Nitin Shingate:
Secure healthcare data and reduce compliance scope
The risks facing healthcare data today are too great to ignore, and the consequences too costly to leave to chance. Reacting after something goes wrong is not enough. Protecting healthcare data means staying ahead – before risks turn into headlines.
Skyflow’s Data Privacy Vault is purpose-built to help healthcare organizations isolate, protect, and govern sensitive data while dramatically reducing compliance scope. With Skyflow, you can simplify your architecture, enforce fine-grained access controls, and maintain the highest standards of privacy without disrupting care.
Ready to strengthen your data security strategy?
Visit Skyflow for Healthcare to see how we help organizations like yours stay secure, compliant, and future-ready.
