A Guide to Healthcare Data Privacy and Compliance
Companies of all sizes are looking to build data privacy, security, and compliance into their architectures to gain the benefits of digital transformation while protecting sensitive data. Here’s a practical guide for healthcare innovators to protect the privacy of sensitive healthcare data.
Cyberattacks are on the rise. Seven out of the 14 biggest healthcare data breaches have occurred in the last three years.
As more healthcare products move to the cloud, the old security model of restricting physical access to an on-prem server or focusing on the security of a network perimeter no longer works.
Your product isn’t safe until sensitive health data – such as personal health information (PHI) and PHR identifiable health information – is isolated and secured. That’s why you should architect proactive security and data privacy controls into your product to enhance the security and privacy of sensitive data.
In this article, we’ll look at the challenges companies face when providing effective data privacy and security for sensitive health data like PHI, strategies that companies can use to improve data privacy and ease compliance, and how Skyflow Data Privacy Vault makes it easier to address these challenges and embrace these strategies.
How GoodRx Protects Billions of Sensitive Records with Skyflow. Watch now →
The Challenges of Effective Healthcare Data Privacy and Security
Increasingly sophisticated cyberattacks, inadequate compliance requirements, and uncertainty caused by new data privacy laws make it harder to secure the sensitive data used by your healthcare product.
Let’s take a closer look at each of these challenges.
Challenge #1: Increasing Attacks, Costs, and Complexity
Over the last five years, an overwhelming majority of healthcare data breaches have been caused by hacking incidents. You can no longer afford to ignore such incidents because each healthcare data breach costs over $10 million on average. As data breaches continue to increase in number and complexity, your healthcare offering needs to be more secure and resilient than ever before.
Challenge #2: Compliance Requirements Alone Can’t Counter Cyberattacks
Mandatory compliance regulations such as HIPAA and ISO/IEC 27001 provide a framework to improve data privacy as well as security. But these regulations from 1996 and 2005, respectively, aren’t up to the task of countering modern cyberattack threats.
For instance, HIPAA doesn’t require an upfront certification from a third-party security assessor. As a result, companies often don’t discover vulnerabilities in their data operations until they face a cyberattack or data breach. So instead of relying on HIPAA guidelines alone, companies should look at their internal quality management systems holistically and implement security procedures. They should also be sure to document the flow of sensitive healthcare data through their systems and trusted third party services – and conduct periodic HIPAA risk assessments.
Challenge #3: Uncertainty and Ambiguity Surrounding Data Privacy Laws
Each government is forming its own rules and regulations around data privacy. New data privacy laws such as the EU’s GDPR, Indonesia’s PDP, and Canada’s PIPEDA have all gone into effect in the last several years. Countries like India are on the verge of creating new data privacy requirements for sensitive data. And other countries, such as the United States, are passing state-level data privacy laws like California’s CCPA (amended by CPRA), or considering new national data privacy laws.
This ever-shifting landscape can be a source of uncertainty. For example, if the United States passed a data privacy law with a strict data residency requirement tomorrow, then you might not be able to send sensitive user data to a product analytics tool based in the UK. No law is final until it’s passed, and even then there’s a process of interpretation and rulemaking by enforcement agencies to resolve ambiguities. So, it’s uncertain how new data privacy laws might affect your business operations and data systems, and such uncertainty creates headaches for global businesses.
For example, TikTok is now setting up a European data center to comply with GDPR. But not all businesses can afford to replicate their data operations across all their business locations. And even if businesses can afford geo-replication, they would still be better off with more cost-effective ways to honor data residency requirements.
How GoodRx Protects Billions of Sensitive Records with Skyflow. Watch now →
7 Ways to Improve Healthcare Data Privacy and Compliance Using Skyflow
Follow these seven steps to provide effective data privacy and security for any sensitive healthcare data that your business handles:
1) Meet Data Privacy and Residency Requirements
In the last decade, many countries have either passed new data privacy laws or strengthened existing laws, and as a result over 100 countries now have data privacy laws or regulations. Countries like Australia, Brazil, Canada, the European Union, and The United Arab Emirates have all created new data protection laws, or revised their existing laws.
Your business needs to comply with data privacy and data residency requirements in the jurisdictions where you operate. To comply with all these evolving privacy laws, you need to store, process, render and transfer sensitive user data within the country or region where this data originates, ideally inside a secure environment that keeps this data within that location. That way, you don’t have to worry as much about constantly evolving laws and regulations because you’re already well-positioned for compliance.
One option to honor data residency requirements is to geo-replicate your data systems across several regions. But geo-replication comes at a steep infrastructure and maintenance cost, as you can see from the following example infrastructure for a global company that operates in the EU and Brazil, but must keep sensitive data within each of these regions:
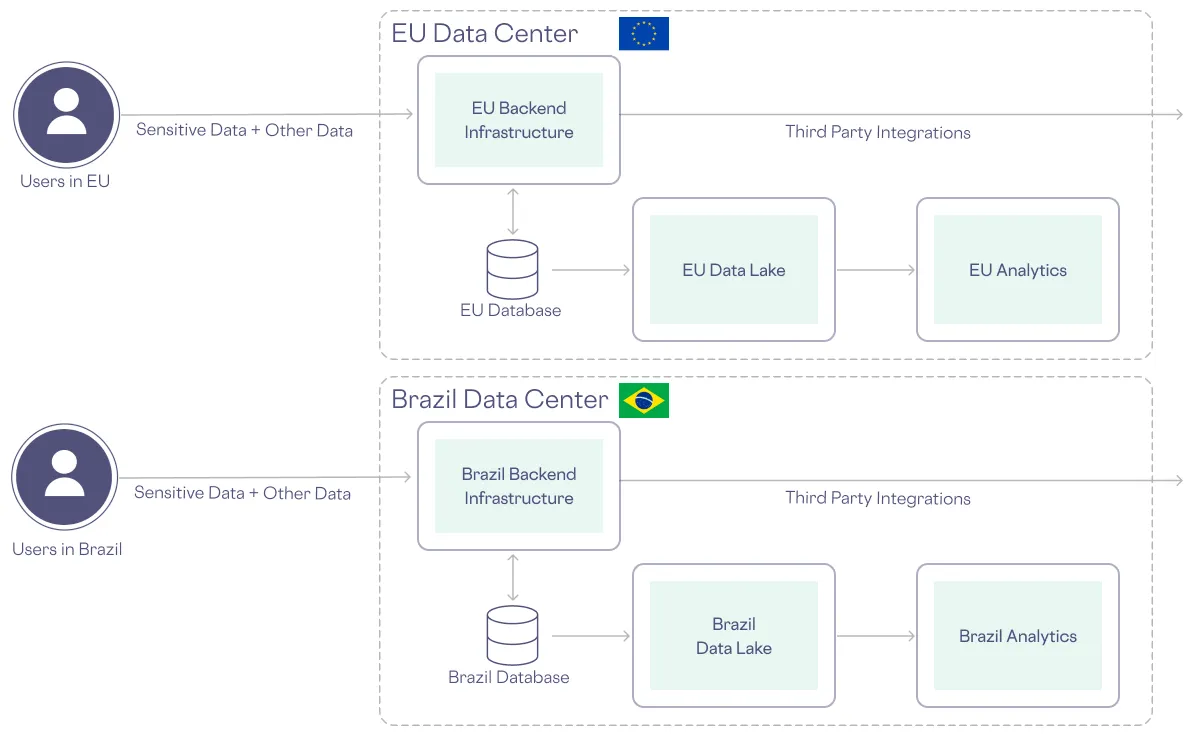
It also leads to data silos and impedes global data analysis.
The more effective alternative is to use a data privacy vault to store sensitive data in its country of origin and avoid replicating your architecture, as shown below:
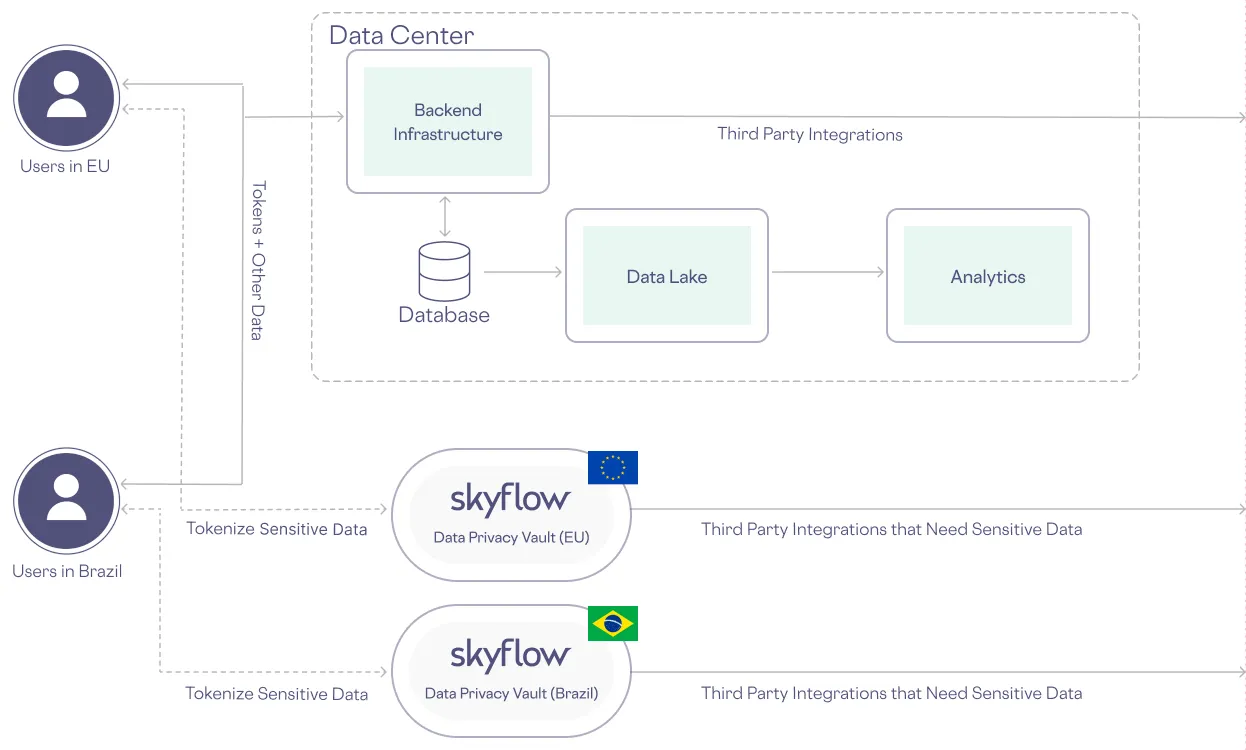
2) Map Where Sensitive Data Is and Where It Goes
You should understand where your sensitive PHI data gets stored and know which tools use this data. To support critical workflows and evolving business requirements, your team adopts many apps. But today, many businesses adopt SaaS apps without the full knowledge of their security teams, causing sensitive data to be stored and processed in unmapped locations and contributing to sensitive data sprawl.
To retain visibility into the location and uses of sensitive data, make sure that you can always answer the following questions:
- Where is your organization’s PHI stored?
- Which tools and locations does sensitive PHI get sent to?
- What guardrails have you put in place to prevent sensitive data sprawl?
- How will you make sure that your product meets data privacy requirements?
3) Isolate, Protect, and Govern Sensitive Data
You should avoid storing plaintext sensitive PHI records in the same database with other non-sensitive application data. Instead, you should isolate and protect your sensitive data inside a separate, secure, and isolated location like Skyflow Healthcare Data Privacy Vault.
Isolating sensitive data inside a vault also helps streamline all your PHI data requests and lets you audit those requests in one place: the vault.
With this approach, you no longer store plaintext sensitive data in systems like your billing software and analytics. Instead, you isolate all sensitive data in Skyflow Vault and configure fine-grained access controls to govern access to sensitive data Skyflow’s API.
Following the principle of least privilege, each system that requires sensitive data only has access to the minimum amount of data that’s required for a given workflow, so if your billing software only needs the last four digits of a customer’s social security number (SSN), Skyflow provides just those last four digits, not full SSNs. Similarly, your analytics only needs de-identified data, not plaintext sensitive data. So, you can reduce your compliance scope by de-identifying sensitive data in your analytics pipeline and storing plaintext sensitive data in a data privacy vault. This reduces your compliance scope while preserving utility for da
Following the principle of least privilege, each system that requires sensitive data only has access to the minimum amount of data that’s required for a given workflow, so if your billing software only needs the last four digits of a customer’s social security number (SSN), Skyflow provides just those last four digits, not full SSNs. Similarly, your analytics only needs de-identified data, not plaintext sensitive data. So, you can reduce your compliance scope by de-identifying sensitive data in your analytics pipeline and storing plaintext sensitive data in a data privacy vault. This reduces your compliance scope while preserving utility for data analytics.
4) Implement Fine-grained Access Controls
Fine-grained access control is a method for providing highly granular control over who can access certain data, and in which format. Because fine-grained access control provides more nuanced control over data access than generalized (or coarse-grained) access control, it is well-suited for managing access to sensitive data.
A rule implemented with fine-grained access control can be simple – consider the following examples:
- Restrict access to only the last four digits of a customer’s social security number (SSN) for identity verification
- Limit which phone numbers customers or gig workers have access to, and for how long, preventing potential misuse
With fine-grained access control, you can implement the principle of least privilege to avoid the many issues that arise when users and systems have overly-broad access to sensitive data.
With fine-grained access control, you could configure rules like the following for a hospital system:
- Patient care providers are granted access to patient medical records, but not to their contact details
- Front desk support staff have access to patient contact details, but not their medical records
This means that neither patient care providers nor support staff have access to all of a patient’s PHI, as shown below:

One option is to engineer this logic into your product. But, this approach can distract your engineering team from building and improving your core product – and can be costly to design, build, and maintain. The other option is to use a data privacy vault that lets you define fine-grained access control.
5) Use Polymorphic Encryption
Encrypting all sensitive data helps to protect data privacy. But most encryption techniques render encrypted data unusable until it is decrypted. Polymorphic encryption solves this issue by allowing certain operations on fully-encrypted data, so you can run certain operations like aggregate analytics without exposing sensitive data.
So, for example, you can use a data privacy vault with polymorphic encryption to encrypt a Social Security number (SSN) and later run identity verification checks by comparing the last four digits provided by a customer to the last four SSN digits stored for that customer in the vault. Similarly, phone numbers can be polymorphically encrypted to let you count the number of patients residing in each area code.
6) Redact Sensitive Data
You can minimize the risk of exposing sensitive data by simply redacting (or masking) it. Similar to the process of concealing a patient’s name or Social Security number on a physical record, you can use a tool like Skyflow to mask sensitive data records either entirely or partially. For example, an analyst for a healthcare provider might have access to full names and partial dates of birth, but no access to SSNs, as shown in the following illustration:
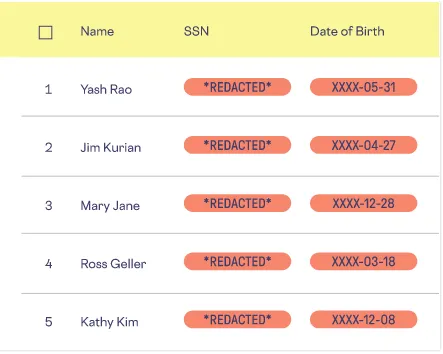
Skyflow lets you fully mask any type of sensitive data, including patient names, insurance information, or contact details. At the same time, it also keeps those data usable for downstream analysis, so you can obtain insights into aggregate patient behaviors, like drug dosage trends.
7) Share Sensitive Data Securely
Tokenization is a method to replace sensitive data records with random tokens. Tokenization techniques reduce the risk of data breaches and help you prevent data sprawl without sacrificing data usability. And they help you securely share sensitive data directly from your vault with trusted third party services without handling that data directly or impacting your compliance scope.
Innovate Quickly Without Compromising on Privacy
Isolating sensitive data, protecting that data with best-in-class encryption and tokenization, and creating fine-grained access controls is a costly and long-drawn process if you try to build it yourself. This makes it important to carefully consider whether to buy a data privacy solution or build it yourself.
Instead of building a data privacy solution yourself, you can use Skyflow Healthcare Data Privacy Vault to save you several years of engineering effort and start preserving patient data privacy today.
For more information, register for our on-demand webinar: The Healthtech Innovator’s Guide to Data Privacy, Security, and Compliance.

