How to Navigate the DOJ's Bulk Sensitive Data Transfer Rule
DOJ Bulk Data Rule implementation guide for enterprise technical leaders facing the October 6, 2025 compliance deadline. Learn CISA security requirements and data de-identification techniques.
October 6, 2025. That's when the Department of Justice (DOJ) bulk sensitive data transfer compliance requirements for due diligence, audits, and reporting become mandatory. Legal teams have already spent months understanding the regulations. Engineering teams must now implement data processing techniques that prevent re-identification of individuals while maintaining business operations.
A leading American financial services company with global operations thought they were compliant with the DOJ Bulk Sensitive Data Rule (Executive Order 14117). Strong role-based access controls. Encrypted databases. Comprehensive audit logs. They manage data sovereignty requirements effectively through traditional segregation approaches.
Then their legal and data privacy leaders explained how the DOJ rule made them rethink their data security and privacy strategy: "These updated compliance requirements go beyond traditional data sovereignty approaches. System connectivity to databases containing covered data can create compliance exposure. Data minimization requirements mandate use of advanced privacy-enabled governance systems to achieve privacy-safe fine-grained data authorization. Conventional data systems simply do not provide such capabilities."
This creates a massive operational challenge for global enterprises. Teams in different regions who collaborate on datasets involving personal identifiers will now need to implement strong controls to safeguard against unintended transfer of data to covered entities .
The challenge isn't security controls. The challenge isn't understanding the regulations. The challenge is architecting systems that can handle complex privacy protection in these transactions while maintaining operational efficiency for global teams.
The Core Dilemma Facing Enterprise Technical Leaders
The DOJ Bulk Data Rule joins a worldwide trend of data protection regulations that create architectural challenges traditional security systems do not address. Like India's DPDP Act and Europe's GDPR, each new law introduces requirements for preventing data breaches through isolation, limiting data use to stated purposes, and granting individuals rights over their data.
Executive Order 14117 addresses "restricted transactions" (employment agreements, vendor agreements, and investment agreements with countries of concern or covered persons) that could provide access to bulk U.S. sensitive personal data. Companies can engage in restricted transactions but must implement CISA security requirements that prevent covered persons from accessing data that is "linkable, identifiable, unencrypted, or decryptable using commonly available technology."
The De-identification Requirement
Enterprises need data processing techniques that eliminate linkability to U.S. persons while maintaining operational utility for legitimate business purposes. CISA requires organizations to "implement a combination of mitigations, which taken together prevents access to covered data that is linkable, identifiable, unencrypted, or decryptable using commonly available technology."
"The bulk data order challenges the value of a global data platform if data cannot be shared globally," explained the head of privacy engineering at the financial services company. This captures the technical implementation challenge: companies need data processing techniques that eliminate linkability to U.S. persons while maintaining operational utility for legitimate business purposes.
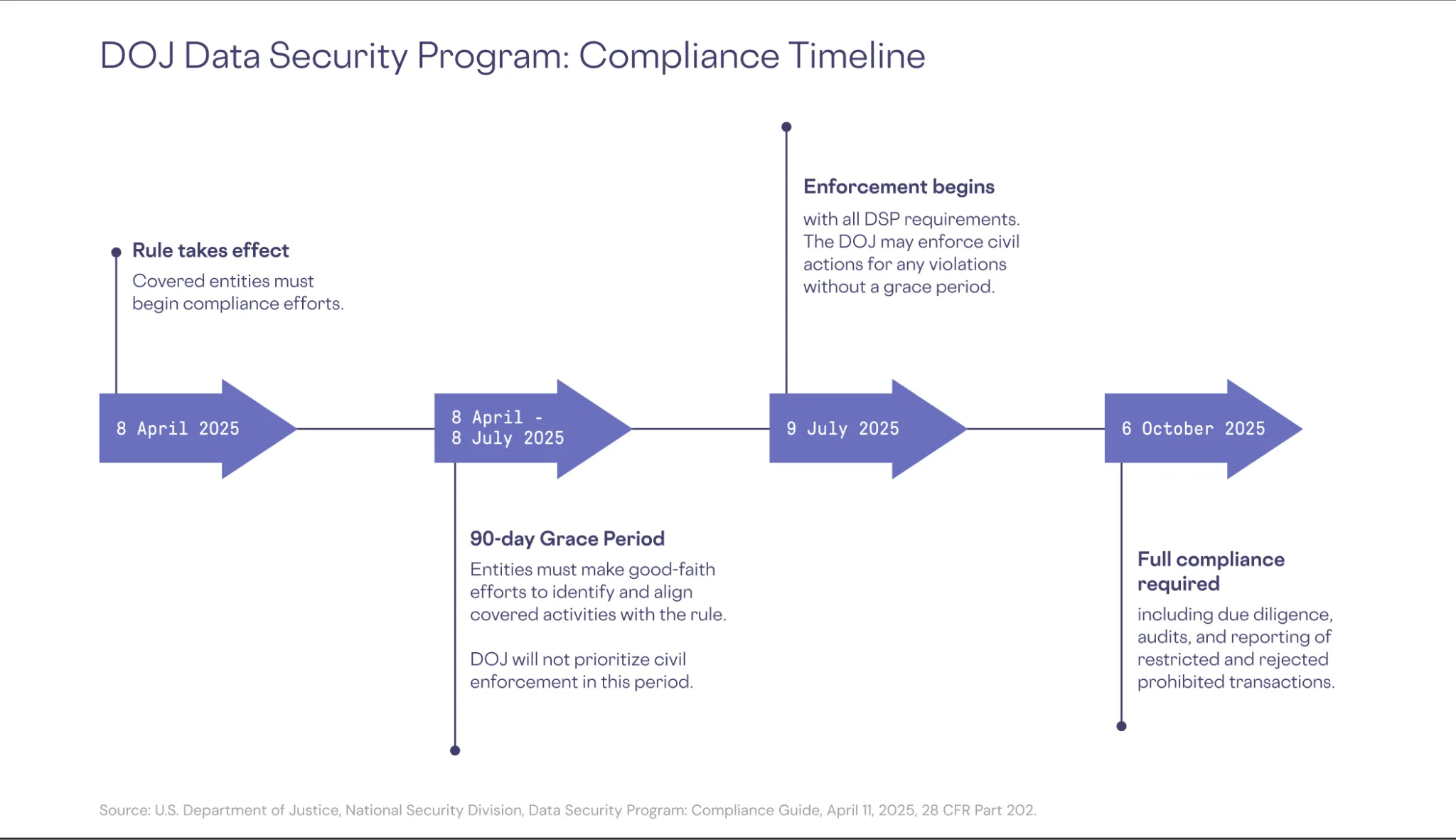
Critical Compliance Timeline
- April 8, 2025: Data Security Program (DSP) became effective
- July 8, 2025: DOJ's 90-day grace period ended
- October 6, 2025: Due diligence and audit requirements become mandatory
Beyond Basic Data Protection: The Re-identification Challenge
The Executive Order's core requirement goes beyond traditional database security: prevent anyone from looking at datasets and re-identifying individuals. Even consistent tokenization can reveal outliers and patterns that expose personal identities. This challenge requires truly unlinking data from real persons while maintaining operational usability.
Traditional anonymization techniques may not meet the Executive Order requirements. Companies must implement approaches that prevent data re-linking while preserving analytical utility for legitimate business operations.
Technical Implementation Requirements
CISA creates two categories of security requirements that enterprises must implement to achieve proper de-identification:
Organization and System Level Requirements
(Standard controls that most platforms already handle)
- Organization-level: Maintain an up-to-date asset inventory, assign clear cybersecurity accountability roles, manage vendors/suppliers, conduct risk assessments annually, and maintain an incident response plan.
- Governance: Enforce vulnerability management (patch/remediate within set timeframes) and control network topology/changes through documented approval processes.
- System-level: Implement strong access controls (MFA or long passwords, deny-by-default, prompt revocation of access), manage credentials/identities, and restrict unauthorized hardware/software.
- Monitoring: Collect and securely retain system logs for visibility, audit, and accountability.
- Change & Configuration Management: Require approvals for new hardware/software and enforce secure default configurations on covered systems.
Data-Level Requirements
(To be based on dataset)
CISA specifies techniques companies must implement:
- Data Minimization: Collecting, using, and retaining only the minimum amount of personal data necessary to achieve the intended purpose. End-to-end data minimization ensures that at every stage: collection, use, and retention, personal identifiers are limited strictly to what the system requires, and nothing more.
- De-identification: Process data to "render it no longer covered data by removing the linkability to U.S. person entities" through techniques like "aggregation, pseudonymization, de-identification, or anonymization." When sufficiently implemented, "data must not be re-identifiable to ensure U.S. person identities cannot be inferred or extrapolated.
- Comprehensive Encryption: Encrypt covered data during transit and storage with key management requirements including "covered persons must not be authorized to have access to encryption keys" and "do not store encryption keys in a country of concern."
- Privacy Enhancing Technologies (PETs): Apply techniques like that process covered data without revealing information "that could reasonably likely be used to reconstruct covered data."
Why Current Security Approaches Fail
The financial services company's legal team initially thought existing security and privacy controls would fulfill the requirements. The technical reality revealed new requirements altogether.
Access Control Isn't Data Control:
- Role-based access controls manage who can query systems. Data privacy requirements need data-level controls that travel with information across applications, databases, and cloud services.
- Traditional security models protect systems. The new model requires protecting data.
- This architectural difference forces fundamental changes. Companies cannot retrofit data-level controls onto system-level security.
- The protection must be built into how data gets stored, processed, and transmitted.
Compliance Requires Architecture, Not Additional Tools:
- Adding more security tools does not address the core requirement: preventing access to data that is linkable, identifiable, or decryptable.
- The solution requires rethinking data architecture to achieve compliance without disrupting business operations.
Given these architectural challenges, companies need systematic approaches to achieve compliance.
Implementation Framework for DOJ Compliance
Companies need clear approaches to Executive Order compliance implementation:
Phase 1: Data Mapping and Classification
Identify transactions ( dataset transfers ) impacted by Executive Order requirements across all systems. Particularly evaluate ones that have direct/indirect links to Covered Persons and Countries of Concern (China, Cuba, Iran, North Korea, Russia, and Venezuela.)Determine which datasets create re-identification risks beyond basic anonymization. Work with legal to distinguish between prohibited, restricted and exempted transactions based on data sensitivity, business requirements and the rules from the Executive Order.
Phase 2: Data Minimization Decisions
Define the minimum set of personal identifiers required to share with partners, vendors, and outsourcing providers. Select appropriate de-identification capabilities to balance operational utility with compliance requirements. Evaluate available custom processing technologies for data de-identification through advanced custom processing.
Phase 3: Access Control Policies
Configure who sees what data attributes across different organizational roles and functions. Implement governance through centralized vault architecture rather than distributed system-level controls. Different tokenization strategies allow organizations to make granular decisions about data visibility.
Phase 4: Integration Planning
Early data ingestion is key to prevent sensitive data sprawl across multiple systems. Proof-of-concept implementation with solution architect support to validate approach before full deployment.
Security and Privacy Platforms That Address Root Causes
Companies exploring DOJ compliance face choosing between retrofitting existing systems or implementing platform architecture that addresses requirements systematically.
Skyflow's Extensible Platform Approach
Skyflow provides building blocks that allow companies to design custom privacy approaches using core tokenization, encryption, and access control technologies. Rather than one-size-fits-all solutions, the platform’s extensible architecture enables customers to plug-in custom solutions to address specific regulatory and operational requirements.
The data privacy vault architecture handles both standard and advanced requirements: out-of-box controls for encryption and access management, plus extensible capabilities for complex de-identification challenges that prevent data re-linking.
Advanced Tokenization Strategies
Skyflow enables companies to choose appropriate tokenization approaches:
- Random tokens for true data randomization that prevent re-identification
- Format-preserving tokens for application compatibility that maintain operational workflows
- Transient tokens for highly sensitive in memory only data for secure processing
Policy Based Access Control
Once companies define policies for data protection and access, Skyflow implements them through platform capabilities rather than custom development. Organizations configure different tokenization approaches, allowing granular control over data visibility across business functions.
Polymorphic Encryption for Operational Utility
Unlike traditional encryption that makes data unusable, polymorphic encryption enables querying and analytics without exposing sensitive information. AI models train on protected datasets. Analytics generate insights without compliance risk.
Architecture Determines Compliance Capability
Enterprise database architectures may not meet DOJ requirements for preventing access to data that is "linkable, identifiable, or decryptable." Audit logging needs data-level granularity that most systems do not provide. Encryption key management requires geographic separation that retrofitting cannot easily achieve.
The October 6 deadline is approaching fast. Companies need architectural solutions that can be implemented quickly rather than taking the custom development route..
Skyflow provides SOC2 Type 2, ISO 27001, and PCI Level 1 certifications that enterprise audit teams require. The platform supports bring-your-own-key capabilities (BYOK) and automated key management that meets DOJ separation requirements.
Skyflow’s Data Privacy Vault architecture allows companies to:
- Isolate sensitive data across multiple cloud regions without platform fragmentation.
- Govern access through centralized policy management that integrates with existing data catalogs.
- Protect data with tokenization that prevents re-identification while maintaining utility
- Maintain operations across global business functions without compliance friction
Key Takeaways for Technical Leaders
- DOJ rule allows restricted transactions with countries of concern through proper de-identification of bulk sensitive data
- Advanced de-identification needs specialized tokenization and anonymization platforms, while standard security tools handle encryption and access controls
- Data-level controls must travel with information across systems, not just protect system perimeters
- Implementation requires clear framework including data classification, minimization decisions, access policies, integration planning
- October 6 deadline creates urgency for architectural solutions rather than custom development
Take Action
Ready to transform your data architecture to meet the DOJ Bulk Sensitive Data order?
Schedule a demo and explore reference architectures with the Skyflow team

