Sensitive Data Protection and Data Residency In Australia
Protecting sensitive data is a problem faced by organizations worldwide, as demonstrated by the ongoing fallout from recent data breaches in which Australian residents had their personal data stolen. So, how can businesses there and elsewhere protect the privacy of sensitive data and meet healthcare data residency requirements?
With the increasing frequency and size of data breaches, companies in Australia are looking to improve their security and privacy posture so they can protect their customers’ most sensitive data – data like names, email addresses, dates of birth, and medicare card numbers. Increased fines make it even more urgent to find solutions to protect the privacy of sensitive data.
In this post, we’ll look at recent developments in Australia and the law recently passed there to increase fines for serious and repeated data breaches. We’ll also look at how Skyflow Data Privacy Vault can help companies improve the privacy and security of sensitive data.
Using a data privacy vault is a critical step to help companies improve their security and privacy posture, while also helping companies that handle healthcare records in Australia to manage data residency.
The State of Data Privacy in Australia
For many years, Australia was like a lot of other countries: legal penalties for mishandling sensitive data or losing customer records in a breach were too small – insufficient to drive significant investment in ensuring the privacy and security of sensitive customer data.
With maximum fines for data breaches long capped at A$2.2m, many companies considered such incidents disruptive and unpleasant, but the penalties themselves weren’t enough to inspire radical action. They were widely viewed as manageable business expenses.
All of that changed in 2022 when a massive data breach at Australian telecom Optus was followed weeks later by another massive breach at Medibank, Australia’s largest health insurer. Over the course of nearly two weeks, Medibank’s customer records were compromised, resulting in the theft of 9.7 million current and former customers’ sensitive data. Medibank saw an immediate 20% drop in its stock price, but the full cost of this breach to the company isn’t yet known.
And, for the victims of this identity theft – Medibank’s customers – the nightmare has continued, as their sensitive data was dumped on the dark web. One immediate consequence of this is that many Virgin Australia customers who were also Medibank customers had their accounts locked as Virgin tried to protect itself from fraudulent logins.
The public outcry was immense, and the response from Australia’s government was appropriately strong and swift.
Australia Raises Data Breach Penalties, Putting Data Privacy and Protection in Focus
Australia’s parliament decided that letting data breaches be a cost of doing business was no longer acceptable, so they passed a bill that increased these fines immensely. What was once a maximum fine of A$2.2m is now a fine of A$50m – or more.
In fact, now the fine for “serious” or “repeated” data breaches is whichever of these numbers is greatest:
- A$50m
- 3x the value of any benefit obtained through the misuse of information
- 30% of a company’s adjusted turnover in the relevant period
The effect of this massive increase in fines is to shift the protection of sensitive customer data from a “nice-to-have” to a “must have”.
And of course, these fines aren’t the full extent of the cost and impact on a business. Per IBM’s Cost of a Data Breach 2022 report, customer outreach, remediation, and reputational damage are just a few of the additional costs companies face in the wake of a data breach.
For example, Australian telecom Optus has set aside A$140m for a customer remediation program following their breach.
So, how can companies at Skyflow and elsewhere protect their customers’ sensitive data to protect this vital asset and retain the trust of their customers?
How Skyflow Protects the Privacy of Customer Data
Skyflow Data Privacy Vault isolates, secures, and tightly controls access to manage, monitor, and use sensitive data. Skyflow is certified SOC2 Type2 and PCI Level 1, and eases compliance with any data privacy law, including GDPR and HIPAA. It uses a set of advanced privacy techniques, including advanced encryption, redaction, and access control to isolate, protect, and govern sensitive data.
To learn more about these capabilities and how Skyflow can help you protect the privacy of sensitive data without sacrificing data utility, check out this post from our blog: What is a Data Privacy Vault?
Skyflow offers a wide range of capabilities to protect the privacy and security of sensitive customer data, including:
- Data Governance Engine: How much control do you have over your data if employee credentials are compromised? With Skyflow’s unique data governance engine, you can control who sees what, when, where, and how. You can also add column- and row-level data access controls, based on any combination of policy, role, or attribute; so you can keep your most sensitive data beyond the reach of employees who don’t need it. And with context-aware authorization, you can go beyond the limits of traditional access control.
- Polymorphic Encryption: Encryption-at-rest is required by several industry standards, and it's far better than storing unencrypted data. But in many cases, encryption-at-rest isn’t sufficient. Skyflow’s polymorphic encryption lets you treat each type of sensitive data differently, so when you only need the last four digits of a customer’s medicare number, that’s all you decrypt. And, it lets you run matching and comparison operations on encrypted data without the need to decrypt it, so you can run credit and KYC checks while keeping sensitive data fully encrypted.
All of that is great, you might be thinking, but what if my customers’ sensitive data is scattered across various systems and services? How can I isolate sensitive data if I need to use it and it’s present everywhere: databases, logs, data warehouses, etc?
This is such a common problem that it has a name: data sprawl. A typical example of an architecture with data sprawl looks like the following:
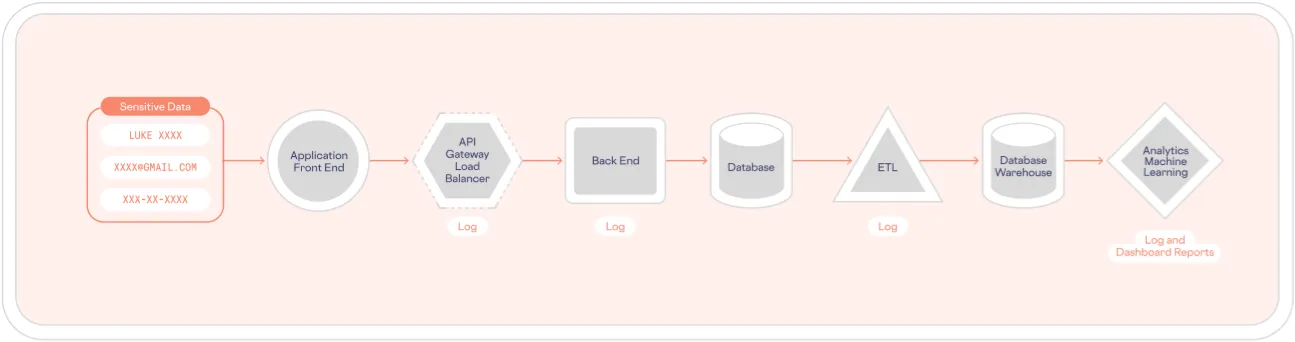
Skyflow’s flexible approach to tokenization lets you prevent data sprawl while putting all of your access controls in one place, where they can be centrally managed. And those databases, logs, and data warehouses? Tokenizing sensitive data gives you “stand-ins” to help with those.
Tokenize and Isolate Sensitive Data
Tokenization is a non-algorithmic data obfuscation technique that swaps sensitive data for tokens. For example, if you tokenize a customer’s name, like “John”, it gets replaced by an obfuscated (or tokenized) string like “A12KTX”.
Because there’s no mathematical relationship between “John” and “A12KTX”, even if someone has the tokenized data, they can’t get the original data from tokenized data without access to the tokenization process. So, even if an environment populated with tokenized data is breached, this doesn’t compromise the original data.
By using Skyflow’s APIs to collect sensitive data and tokenize it, you can manage sensitive data without having your backend systems ever touch it. Instead, your backend manages tokens that point to sensitive data that’s centralized and isolated in your Skyflow Vault.
The result looks like this:
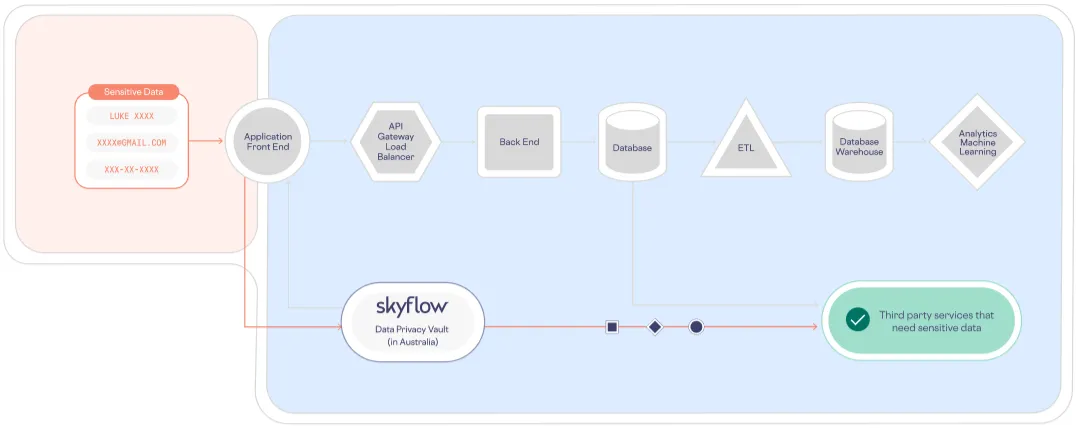
To detokenize sensitive data, your backend provides those tokens to Skyflow, which confirms that your request meets strict zero trust access controls before detokenizing and returning the requested data. You can learn more about our flexible approach to tokenization in Demystifying Tokenization: What Every Engineer Should Know.
How Skyflow Ensures Data Residency for Healthcare Data
Another benefit of isolating sensitive customer data in Skyflow Data Privacy Vault is that it eases compliance with data residency requirements. According to the Personally Controlled Electronic Health Records Act 2012, Australian patient healthcare data is required by law to remain within Australia’s borders.
With all sensitive healthcare data stored in a Skyflow vault located where you need it, it’s easy to stay compliant with data residency requirements in Australia, or anywhere in the world. To learn more about how we can ensure data residency, check out this article from our blog: What is Data, Residency, & How Can a Data Privacy Vault Help?
Skyflow Is In APAC, Ready to Help
Many members of the Skyflow team are located near Australia in the Asia-Pacific (APAC) region, based in our Bangalore office. We're excited to work with you to help you to protect the privacy and security of sensitive data with sales, solutions architecture, and customer implementation teams – all based in APAC.
And with much of our engineering team also located in Bangalore, you won’t have to worry that you’re not getting the same level of service and support that a business in North America would.
Skyflow is built in APAC, staffed up, and ready to help APAC customers protect the privacy of sensitive data.
Final Thoughts
Australia’s multi-million dollar penalties for serious or repeated data breaches are a great reason for Australian businesses to use a data privacy vault to improve their privacy posture.
If you’d like to learn more about how Skyflow can help you protect the privacy and security of your customers’ sensitive data while easing compliance, contact us to learn more.