Introducing the Skyflow Data Governance Engine
Securely storing sensitive data is not enough. The real value comes when you can store and use the data securely, both with a privacy-first design. Today, we’re excited to announce Skyflow’s new Governance Engine, a set of platform features (shared across all our data privacy vaults) that will help you get the most value out of your sensitive data while also ensuring it is kept secure and private. We’re rolling it out today for all customers as part of our launch of the new PII Data Privacy Vault.
There are two basic ideas behind Skyflow Governance Engine, fine-grained access control and fine-grained logging and auditability. With both, our goal is to give you tools that go beyond the basic needs of data security and compliance and allow you to safely utilize your data in your apps, workflows, analytics, data sharing, and more. Read on for all the details on how it works:
Learn how to isolate and secure sensitive data with a vault. Get your guide →
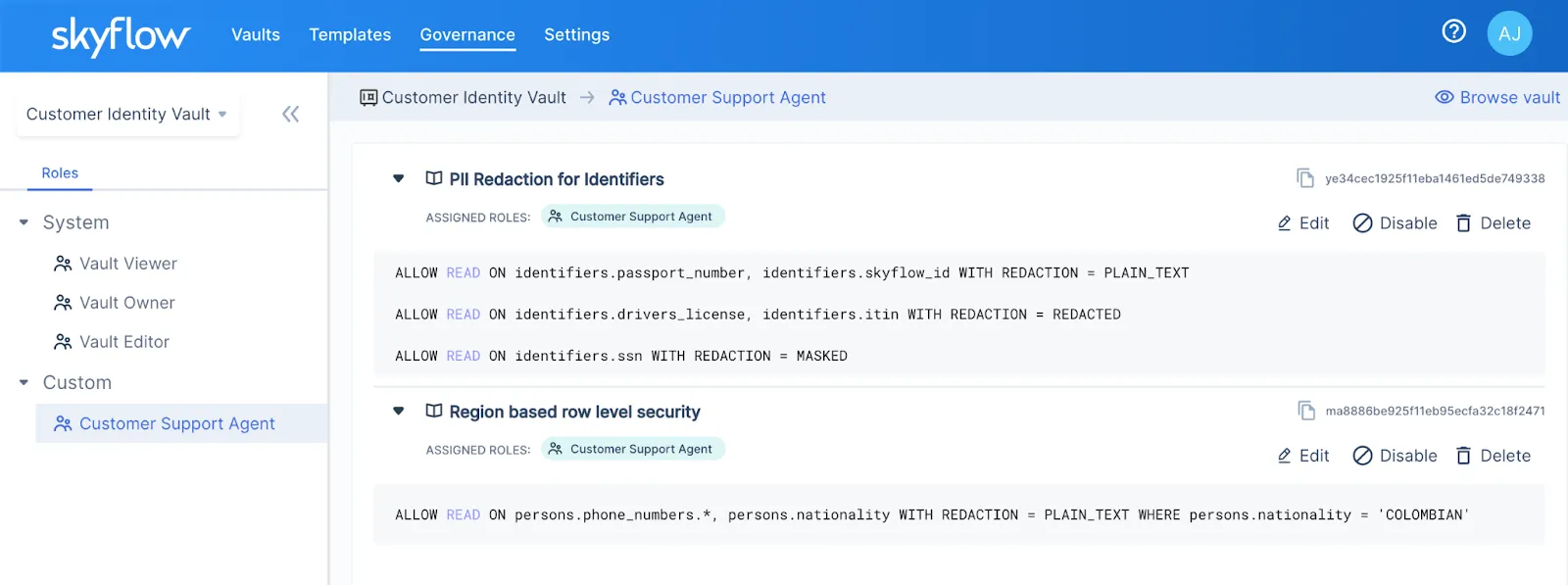
Policy-Based Access Control Model
Skyflow leverages a Policy Based Access Control (PBAC) Model which enables you to enforce fine-grained, event-driven, and condition-based policies to govern access to your vault. You can author policies and then attach them to one or more roles. You can then assign these roles to Users (UI) or Service Accounts (API clients) to enforce granular data access control.
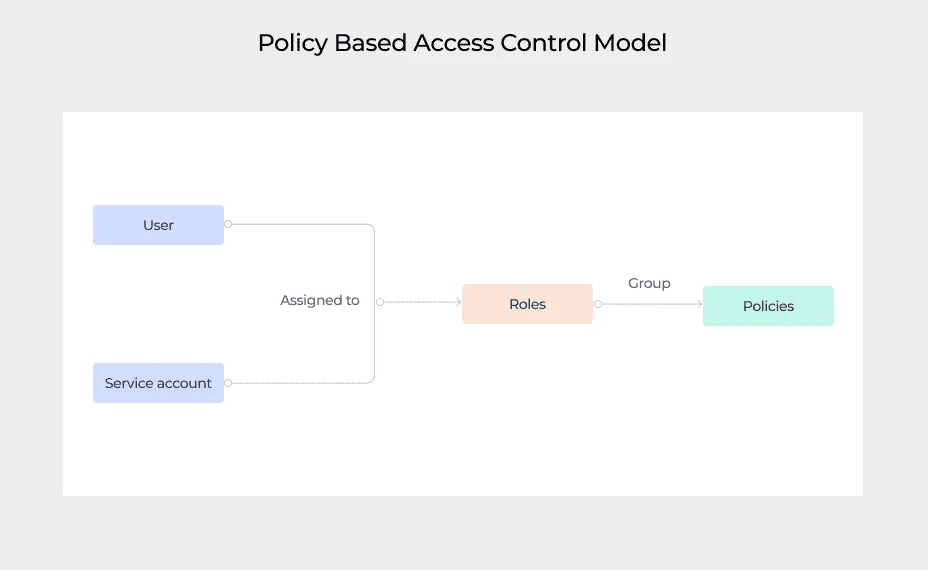
The benefit of this model is that you get the easy manageability of roles in a Role Based Access Control (RBAC) system while preserving the granularity and dynamism of an Attribute Based Access Control (ABAC) system.
Policy Expression Language
We have developed a strongly typed, human-readable policy expression language which is used to author complex, granular data access control rules for the vault. This language makes the experience of authoring policies very easy by using parameterized variables and code snippets so that even non-technical users can author complex policies without any prior context.
The following is a representation of the policy language grammar:
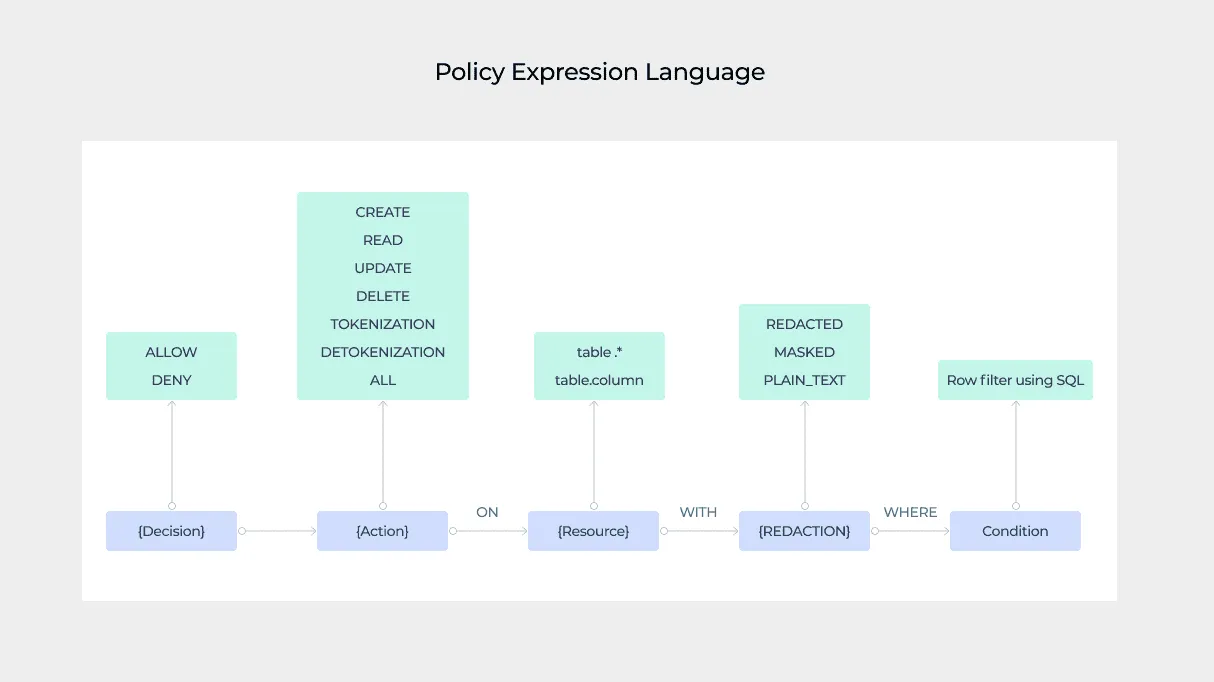
The policy sentence consists of a decision, an action, a resource, and redaction formats when reading data and conditions, all represented as parameterized variables.
Here are some example rules authored using the policy expression language:
Data Minimization with Granular Data Access Policies
Enforcing principles of least privilege is an effective way to reduce your attack surface area when governing access to sensitive data. Additionally, this is a key mandate of the GDPR regulation. User accounts and apps should only have access to the specific fields that they need to perform a legitimate business function.
Skyflow enforces fine-grained and condition-based data access control policies by offering column-level and row-level access permissions and support for SQL WHERE filters.
For example, you may want to enforce a policy where a physician may need to view and edit only the medication column from the patients vault for only those patients that live in California:
Privacy Preserving Data Sharing
Privacy preservation is one of the key value propositions of Skyflow. Skyflow employs Data Loss Prevention (DLP) techniques such as tokenization, redaction, masking, and encrypted operations to preserve data privacy. Skyflow’s governance engine can ensure that the same data is shared differentially based on the identity of the end consumer and the specific business use case.
For example, you may want to enforce a policy where a customer support agent may need to view only the last 4 digits of a consumer’s SSN for identity verification purposes:
Auditing
Skyflow keeps a metadata record of every single data access request so that data admins can audit who accessed what resource and when was the access request made. We audit any changes made to any data access policy. We also provide bulk APIs so that you can load your security information and event management (SIEM) systems with all the audit information from Skyflow for monitoring and tracking.
API-first Design
Skyflow follows an API-first approach to product development. All the features that are available through our UI are also available to all our customers via REST APIs. We also provide language-specific SDKs to enable faster product integration with your tech stack.
Better API Security with Service Accounts
Skyflow leverages the concept of service accounts to represent machine identities for API clients. A significant advantage of using service accounts is that customers can assign the same fine-grained policies that are enforced for users to API clients as well. Other software vendors that use OAuth clients are restricted to using coarse-grained permission models such as OAuth scopes, which act against the principles of data minimization.
Many software vendors use API keys or the OAuth2 client credentials grant type for API authentication. Such modes of API authentication that use static credentials have known gaps and can be easily exploited. Skyflow leverages cryptographically signed JWTs for API authentication in accordance with the IETF OAuth2 JWT profile for client authentication specification. You need to sign the JWT with a private key known only to yourself in order to authenticate service accounts in Skyflow.
Compliance
Skyflow Data Privacy Vault is compliant with PCI, SOC 2, HIPAA, and other regulations out of the box. We are also on track to get HITRUST compliance certified soon. When you use Skyflow to offload the management of sensitive data, you are also offloading compliance requirements to Skyflow which in turn enables you to focus on your customers and their needs.
Conclusion
To see all of these features and more, sign up for a free demo from our sales team. Stay tuned to our blog for the release of more platform features around data governance and beyond.

