Network Tokenization: Everything You Need to Know
Network tokenization is an innovative technology that replaces payment card data with a network-issued token and unique transaction cryptograms. This represents a vast improvement over the more common approach to protecting transactions with tokenization, known as PCI tokenization or vault tokenization. Network tokenization reduces the potential for fraud, improves the merchant and consumer experience, increases approval rates, and reduces overall transaction costs.
Historically, most merchants directly handle sensitive payment card information and adhere to the PCI security standards. This makes them responsible for securely handling, storing, and protecting that data – which can be especially laborious for e-commerce merchants.
Additionally, to authorize a card transaction for payment, multiple hand-offs are required, passing the card number, expiration date, and CVV to various parties involved in the payment transaction. This system presents multiple points of failure that could potentially expose a client’s payment card data.
Network tokenization is a new way to process card payments that helps to keep sensitive customer card data more secure while increasing authorization rates and reducing costs for both card-present and, more recently, for card-not-present transactions.
In this post, we cover everything you need to know about card-not-present network tokenization.
Modern privacy needs modern tokenization. Read the whitepaper →
The Problem with Credit Card Transactions
When a merchant wants to charge a card, the usual workflow is to send an authorization request to a payment processor with the card number, expiration date, CVV, and amount. The payment processor or gateway will pass on the card details to the card network, which will then forward them to the card issuing bank for approval. Then the approval message is sent all the way back to the merchant.
The image below shows how card data flows in a traditional card transaction flow:
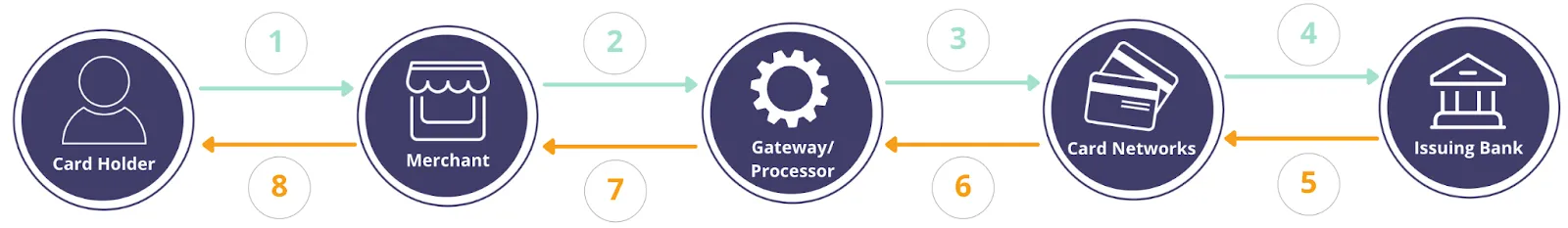
Throughout this process, the card number, expiration date, and CVV are passed from one party to another. Of course, this presents many potential points of failure where this sensitive card data could be exposed.
Several years ago, point-to-point encryption was implemented for most point of sales transactions. This change, along with the more recent EMV standard for chip and NFC payments that’s been widely adopted at the point of sale, greatly reduces fraudulent transaction activity.
As expected, in response to the new card-present security capabilities added by E2EE and EMV standards, fraudsters have shifted to ecommerce.
Ecommerce merchants in the industry have tried their best to keep fraud in check with additional fraud checks that happen as data flows to the payment processor, card network, and issuing bank. The issuing bank will check if the person has the funds for the purchase and whether the card number is valid, and attempt to confirm that no fraud is happening.
When a fraudulent transaction occurs the cardholder initiates a chargeback, and the issuing bank kicks off the chargeback process. Now with EMV and NFC for point of sales transactions, the issuer bears more risk and responsibility for those losses. Unfortunately for merchants, with most card-not-present transactions, the merchant ends up bearing the cost of the fraudulent transaction. If the merchant fights the chargeback, then it will go back to the issuer. This process continues until someone pays for the chargeback.
Both the merchant and the issuing bank have a vested interest in reducing fraud as much as possible to reduce the associated losses and cost to manage the process.
Network tokenization aims to solve this problem by removing the card number from most of the steps in the card transaction data flow and also providing a cryptogram for each individual transaction. This has greatly reduced card-present fraud.
How PCI Tokenization Works
Before getting into the details of network tokenization, let’s first look at PCI tokenization (also known as vault tokenization).
PCI tokenization was introduced by the PCI Security Standards Council as a way to reduce the exposure of card information for merchants. In this approach, the card number is replaced by a token at a specific endpoint instead of across the entire payment ecosystem. This is a technique used by many payment service providers like Stripe, Braintree, Cybersource, and Adyen.
The merchant registers the card number with the payment services vault and the payment service returns a token. The merchant can safely store this token and remain PCI DSS compliant. The payment service is responsible for securely storing the card details in a compliant way.
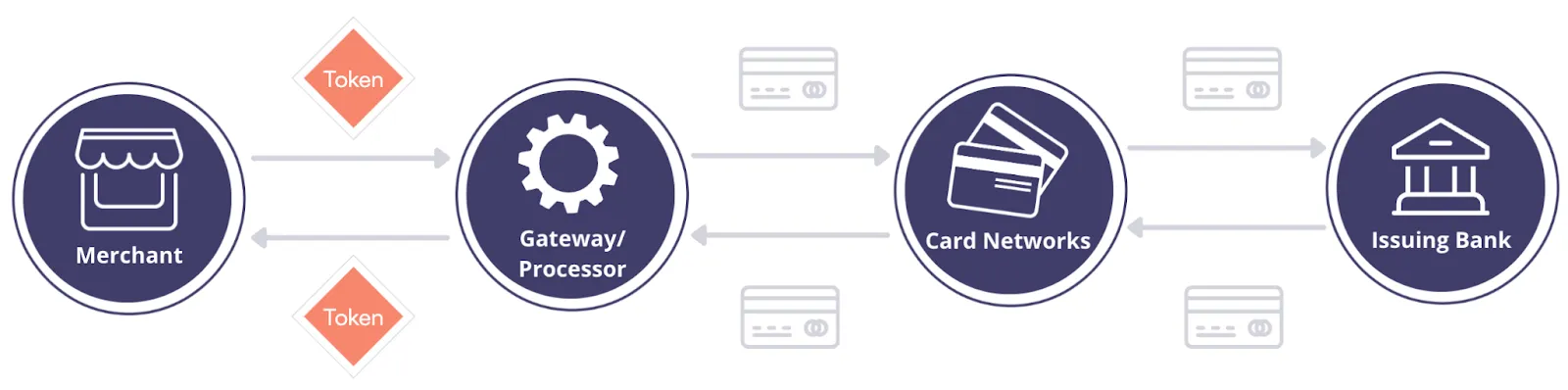
When the merchant wants to issue a transaction against the card, they can pass the token and transaction details to the gateway (processor) as shown above. The payment processor then swaps the token for the card number and passes the card information downstream to carry out the transaction.
PCI tokenization insulates the merchant from having to secure the card details, but there are still many potential points of failure along the way.
Modern privacy needs modern tokenization. Read the whitepaper →
What is Network Tokenization?
Network tokenization is a transformative technology that replaces card details with a network-issued token instead of a payment processor-issued token.
With network tokenization, the network (Visa, Mastercard, or American Express) also generates a cryptogram for each card authorization, adding a second layer of security. One of the major advantages of shifting the token generation down to the network is that now more of the downstream services are insulated from dealing with the actual card information – instead, they just manage tokens.
How are Tokens Issued?
Tokens are issued for a card via a token provisioning flow, as shown below:
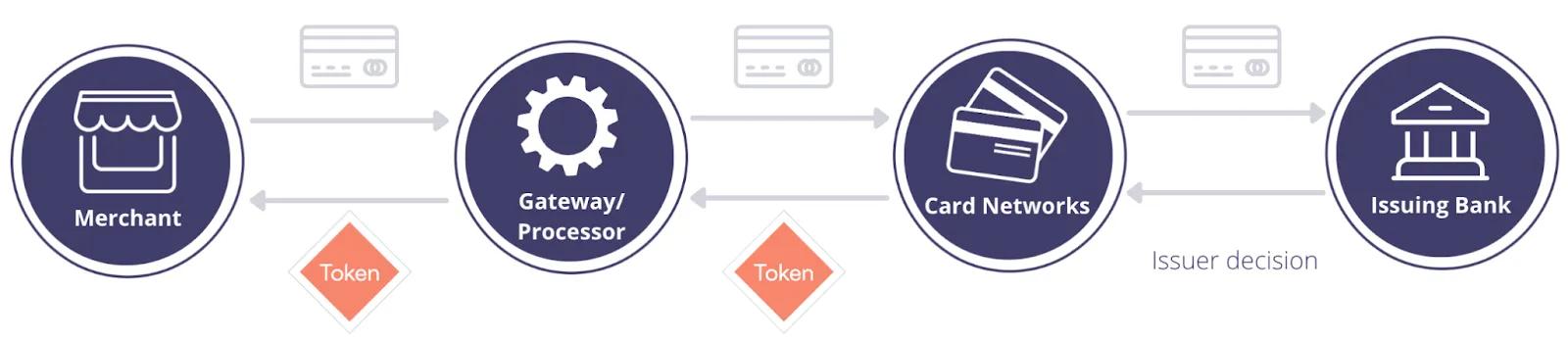
This process follows these steps:
- A customer enters their card details: payment account number (PAN), CVV, and expiry date
- The merchant (token requestor) sends the card information to the token gateway service to request a network token from the card network
- The card network shares the token request with the card issuer (often the consumer’s bank)
- The card network shares the token with the token gateway
- The token gateway shares the token with the merchant or token requestor to store it for future transactions
Each token is unique to the customer, PAN, and merchant. Since the card network is issuing the token, it’s interoperable across the entire payment ecosystem and supports a broader range of use cases than the more common PCI tokenization approach.
Next, let’s take a look at how this works when authorizing a card transaction.
How are Tokens Used for Transactions?
Once a token is provisioned for a card, transactions are carried out using the network token representation of the card rather than the card details, as shown below. In addition, a cryptogram is generated and sent along with the authorization. This cryptogram is unique to the token, merchant, and individual transaction.
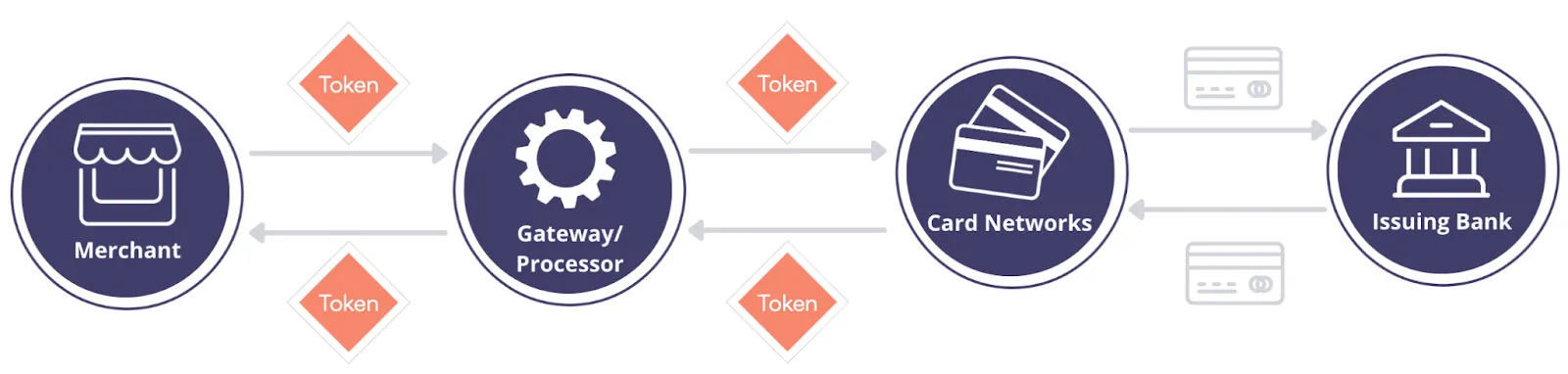
As you can see, the card information is only transacted between the network and the issuing bank. Everywhere else, a network token is used.
This reduces the potential points of failure (or “leakage”), since the amount of PCI data transacted is significantly reduced. This also reduces the rate of fraud because the card details are only being transacted with an associated cryptogram between the card network and the issuing bank, and the card network knows if the card is valid.
Benefits of Network Tokens
Using network tokens helps to keep cardholder information safe and up-to-date, while also offering cost savings and an improved customer experience.
Keeps Cardholder Information Safe
Fraud rates keep on climbing and US merchants are struggling more than ever to prevent fraud from happening. In fact, merchants are spending up to an estimated $3.48 for every dollar of fraud.
The end-to-end security that network tokenization introduces significantly reduces the risk of fraud. Outside of the initial collection point, network tokenization removes the need for merchants to directly handle any sensitive card information. Instead they deal with a network token, which has no exploitable value. Second, the cryptogram further secures the authorization. Visa has seen an increase in authorization rates and a 26% average reduction in fraud as a result of using network tokenization.
Keeps Cardholder Information Up-to-date
Network tokens are persistent tokens for merchants. This means that the merchant will always have one token for a set of cardholder information, even if that information changes.
The card network that maintains the mapping of cardholder information to network tokens updates the mapping on the backend if a change happens. This means that the merchant always has an active card to try based on the persistent token and should experience less churn from inactive cards.
Second, network tokens also support Payer Account Reference (PAR). PAR is designed to ensure that the underlying PAN that was used to support various payment processing and value added services can still be performed without having to rely on the PAN.
Cost Savings
When a card is charged, a merchant typically pays a transaction fee, which is based on an interchange rate and a few other inputs. Fraud rates impact interchange fees, which is why the interchange rate is higher for card-not-present transactions versus card-present transactions. To support the rollout of network tokens and the decrease in fraud rates, Visa announced an average ten basis points reduction in interchange for card-not-present network token transactions in April of 2022. Other networks are expected to follow suit.
Additionally, the industry is expecting a liability shift for card-not-present network tokenization. Traditionally, merchants are responsible for covering fraud charges, but with network tokenization the liability is expected to shift to the issuer, similar to the pattern we saw with card-present EMV transactions.
Improves the User Experience
As mentioned above, since the card network now maintains the mapping between card information and the token, if a card expires or is replaced, the card information is updated automatically. A consequence of this shift is an improved user experience because the customer won’t have to update their card information with the merchant every time it changes. Additionally, this increases authorization rates for merchants, preventing declines due to card expiration, loss, or theft.
How Network Tokenization Works with Skyflow
Skyflow supports network tokenization for Visa, Mastercard, and American Express cards. The integration process for using network tokens with Skyflow is exactly the same as it is for PCI tokenization. Skyflow abstracts away the complexity of integrating directly with each network token service individually, so that provisioning a card or carrying out a transaction requires just a simple API call.
The diagram below shows the provisioning flow for registering a card in exchange for a network token. The client makes a single API call, sending the card information directly from the client application to Skyflow. The card information never touches the client’s backend systems.
Skyflow routes the card to the appropriate token network provider and returns the token, as shown below:
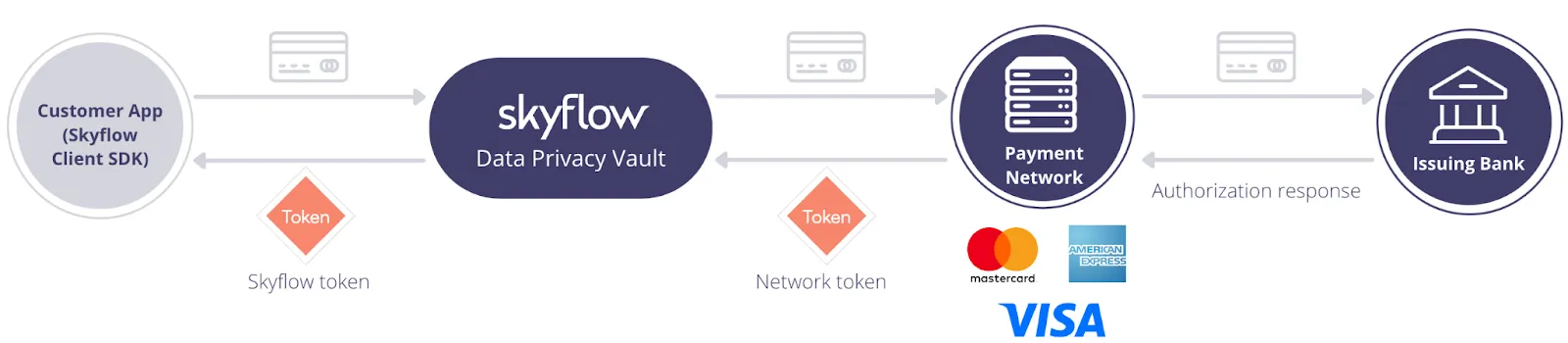
The token can be safely stored by the client. When it’s time to charge a card, the token is used directly with Skyflow’s APIs to carry out the transaction.
Below you can see the data flow when charging a card:
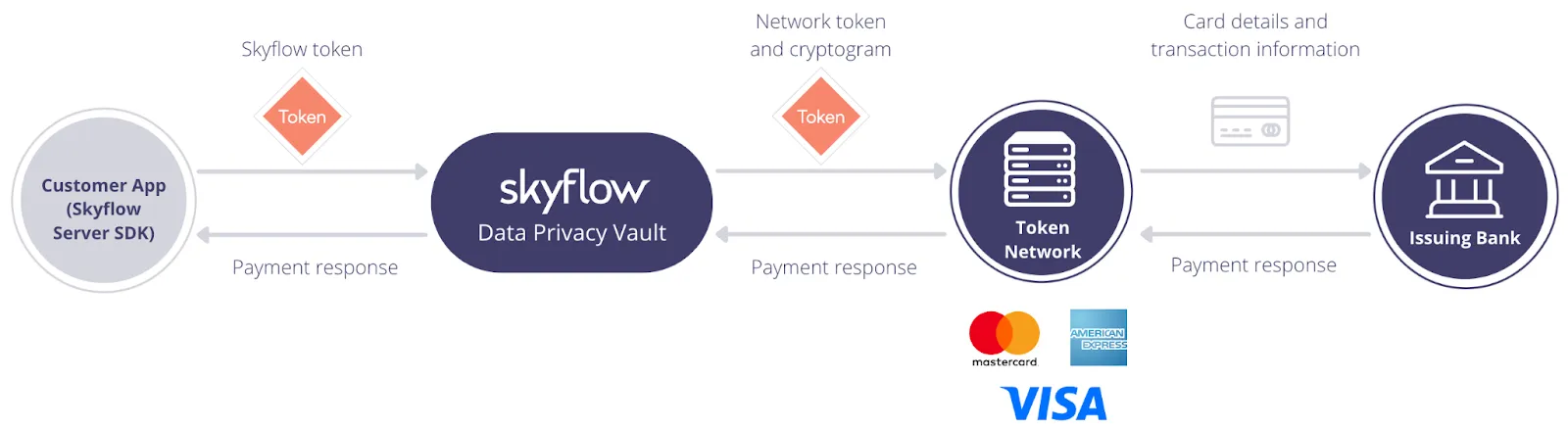
This process follows these steps:
- The client calls Skyflow via a Skyflow SDK with a Skyflow token
- Based on the card’s network, Skyflow retrieves the network cryptogram and network token and passes the cryptogram, network token, and transaction details to the processor
- The processor sends the cryptogram and network token to the payment network
- The payment network exchanges the network token for the PAN and then sends the card information to the issuing bank, who validates the card information and cryptogram, and then charges the card
- The payment response is routed back to the client and the PAN is mapped back to the network token by the network
Final Thoughts
Network tokenization is a fantastic innovation that reduces fraud, decreases costs, and creates a better consumer and merchant experience. With Skyflow, you get all of the benefits of network tokenization, without the complexity of integrating with multiple card network providers.
Skyflow gives you a single point of entry for transactions through Visa, Mastercard, and American Express, as well as the growing number of networks we plan to support in the future. Additionally, Skyflow is an all-in-one data privacy solution that supports the secure storage of sensitive customer data beyond just credit card information, including healthcare data and PII.
If you’re interested in learning more about Skyflow’s network tokenization solution, please contact us to try Skyflow. And if you're an existing customer looking to learn more, please reach out to your Skyflow representative.
