DPDP Rule 6 Compliance: Beyond Basic Protection to Polymorphic Encryption and Advanced Tokenization
(This is Part 2 of our Blog Series: DPDP Act and Rules Preparedness with Skyflow. Read Part 1)
The Digital Personal Data Protection Act, 2023 (DPDP Act) sets a strict standard for personal data security in India. Data Fiduciaries (DFs) are required to take reasonable security safeguards to prevent personal data breach. For the first time, the regulator - the Data Protection Board of India - has spelled out specific technical measures that Data Fiduciaries must implement rather than vague notions of “best practices,” providing clear, enforceable controls defined under Rule 6 of the DPDP Rules.
Compliance with Rule 6 is not optional; failure to implement these safeguards is a significant breach leading to financial consequences that could extend to two hundred and fifty crore rupees or approx. $30M USD. Rule 6 forces a deeper conversation: modern enterprises must move beyond infrastructure-centric protections and adopt architectures that directly safeguard the personal data itself while keeping business workflows functional.
Decoding the Mandatory Technical Requirements of DPDP Rule 6
Rule 6 mandates that DFs implement specific technical and organizational controls, making clear that generalized cybersecurity is insufficient. Also, compliance requires a targeted approach to protecting the data itself by:
- Data Security Techniques: Data must be secured through methods such as encryption, obfuscation, masking or the use of virtual tokens mapped to that personal data.
- Access Control: There must be appropriate measures to control access to the personal data, used by the DF or its Data Processor.
- Visibility and Auditing: Maintain appropriate logs and implement monitoring and review processes to ensure visibility into personal data access. This is essential for detecting, investigating, and remediating unauthorized access, while also preventing recurrence.
- Log Retention: Logs and necessary personal data must be retained for a minimum period of one year to support investigation and remediation.
- Contractual Flow-Down: Ensure appropriate provision for security safeguards are included in the contract with their Data Processors.
What becomes obvious is that Rule 6 is fundamentally about consistent protection and governance of the personal data itself, not just the systems around it.
Why Infrastructure and Network Security Are No Longer Enough
For years, organizations have relied on perimeter tools - firewalls, WAFs, VPC configurations, IAM, cloud posture management to “secure” their environments. These tools remain valuable, but they fail in one critical way: they do not secure the personal data once an attacker, insider, or misconfigured system passes the perimeter.
When personal data routinely travels across microservices, logs, caches, analytics platforms, AI and ML workflows, the perimeter is porous by design. Rule 6 recognizes this reality. Network and infrastructure protections cannot guarantee that personal data is protected and hence the need to consistently encrypt, tokenize, govern, log, or be auditable throughout its lifecycle.
This is where the real challenge surfaces: personal data sprawl. In most organizations, personal data does not exist in one place.
Architecture and Beyond: The Right Solution
In most organizations, personal data does not exist in one place. It multiplies across databases, logs, caches, object storage, analytical tools, AI training pipelines, CRM systems, and third-party integrations and many more. Each location introduces its own security, access control, audit, masking, and encryption gaps.
Technology and implementation details itself is an important focus piece to the success of DPDP Act and Rules compliance. Below are some of the challenges of traditional approaches and the recommendations for using the right technology to meet ALL the requirements.
The Limitation of Basic Encryption
The need for encryption stems from legal mandates and the general requirement to protect sensitive data.
Encryption is a natural starting point and is considered the "first line of defense" for transforming readable text into unreadable ciphertext to reduce the risk of unauthorized access and data breach. However, attempting to apply encryption across a fragmented enterprise infrastructure (the "Just Encrypt Everything" Trap) creates significant technical hurdles:
Performance and Functionality Breakdown: Traditional encryption breaks operations like search queries and even exact match lookups because well-crafted database indices for fast lookups no longer work on encrypted data.
- This forces every lookup to require decrypting the data and perform a full table scan, which is unacceptably slow.
- Traditional encryption breaks search, range queries and joins, stops analytics, and kills AI/ML workflows.
- Some of the fields require preserving the format of the data for ease of transformation, this means additional work and overhead.
Key Management Complexity (KMS): Encryption relies heavily on a key that must be stored and secured. Implementing this properly requires a reliable Key Management System (KMS) to secure, use, and map the keys.
- The engineering task involves supporting the full key management lifecycle, including generating sufficiently long keys, securing storage, and adhering to the security best practice of rotating keys every 6 months.
- Using envelope encryption (where a Data Encryption Key (DEK) encrypts the data, and a Key Encryption Key (KEK) encrypts the DEK) is one example of key management in use. To rotate the DEK keys, without taking application downtime, is a significant challenge.
- To mitigate latency, teams often end up having a cache to reduce the costly trip required to the KMS for every insert, update, and read operation. This defeats the whole purpose of protecting data and takes the problem back to where it was.
Complex Workarounds (DIY): When encryption breaks business logic, engineers are forced to build secondary systems on top of their infrastructure:
- A separate search database (like Elasticsearch) is often introduced to store hashed personal data values to enable quick exact match lookups.
- To support complex queries like substring matches, sophisticated algorithms such as n-grams with rolling hashing or the Rabin-Karp Algorithm may be needed.
- Even after that, relationships between the personal data becomes a very difficult task to establish
Apart from this, other requirements around consent enforcement by purpose and data principal rights aren’t getting solved with these approaches, and also, other data stores like logs, 3rd party SaaS, analytical systems still are open, leading to creating new projects and sub-tasks, and companies caught in a maze.
We haven’t even talked about the topic of unstructured data or AI workflows where personal data is involved.
As you will notice, what looks like a simple encryption project quickly ballooned into a multi-person team and large scale project with a lifetime of maintenance diverting resources away from core product development and innovation.
The Right Approach: The Data Privacy Vault Architecture
The difficulty arises from trying to apply fragmented security and governance controls across a messy, sprawled infrastructure, rather than centralizing control. Skyflow’s Data Privacy Vault architecture provides a mechanism to isolate the sensitive data and apply protection uniformly:
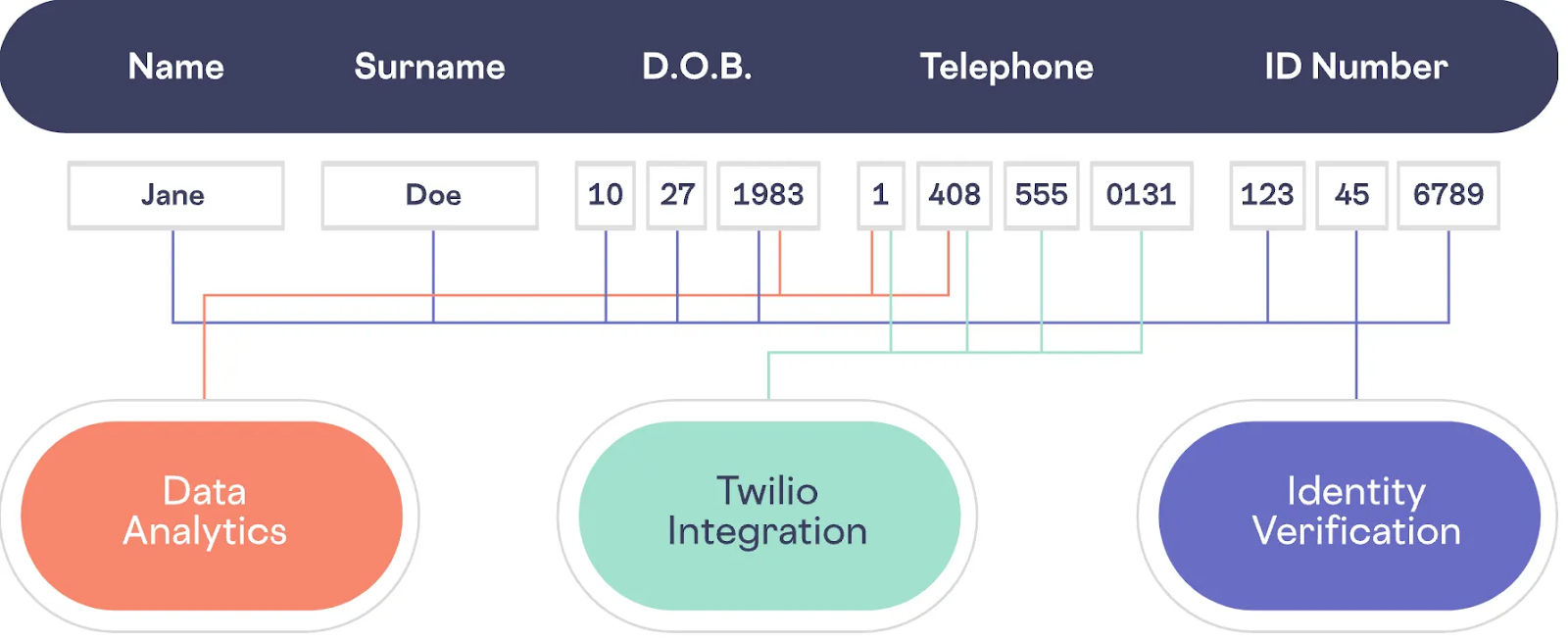
- Isolation: The architecture isolates personal data separate from existing systems (databases, logs, analytics, AI models) and replaces the raw data in those systems with non-exploitable consistent-format preserving tokens. This de-risks the existing application and analytical systems because the personal data doesn’t exist in those layers.
- Polymorphic Encryption: Skyflow uses proprietary technology known as polymorphic encryption to solve the conflict between security and sensitive data utility.
- This technology ensures that data remains encrypted at rest, in transit, and even during runtime.
- Crucially, polymorphic encryption allows operations like search, aggregation, and comparison to be performed on protected data, maintaining full functionality (queries work, analytics run, AI trains safely) without requiring full decryption.
- Centralized Control: The vault centralizes all security controls, including fine-grained access policies, automated key management (BYOK supported), and immutable audit logs, eliminating the need to implement these complex security controls individually across dozens of infrastructure points. Skyflow also helps in establishing the relationship between the personal data types, along with advanced techniques for unstructured data and AI workflows.
Precedent for Isolation: The Data Vault Model
This architectural approach is not novel; it is a proven model successfully implemented in highly regulated sectors where data security is paramount, and now the scope extends to the entirety of personal data.
- PCI Token Vaults: The payments industry mandates tokenization and the use of a secure card token vault to replace 16 digit card numbers with non-sensitive tokens. This technique effectively reduces the security scope and compliance burden for operational systems.
- Aadhaar Data Vaults: In India, a dedicated data vault architecture is already being followed by organizations who store Aadhaar numbers. This ensures the sensitive identifier is isolated, governed, and auditable, permitting compliant re-identification only for legally permissible use cases (e.g., KYC/AML) under strict audit logging.
The Data Privacy Vault generalizes this proven, established, security-first architecture to encompass all forms of personal data, while ensuring business workflows function. making it the optimal framework for holistic compliance with regulations like the DPDP Act.
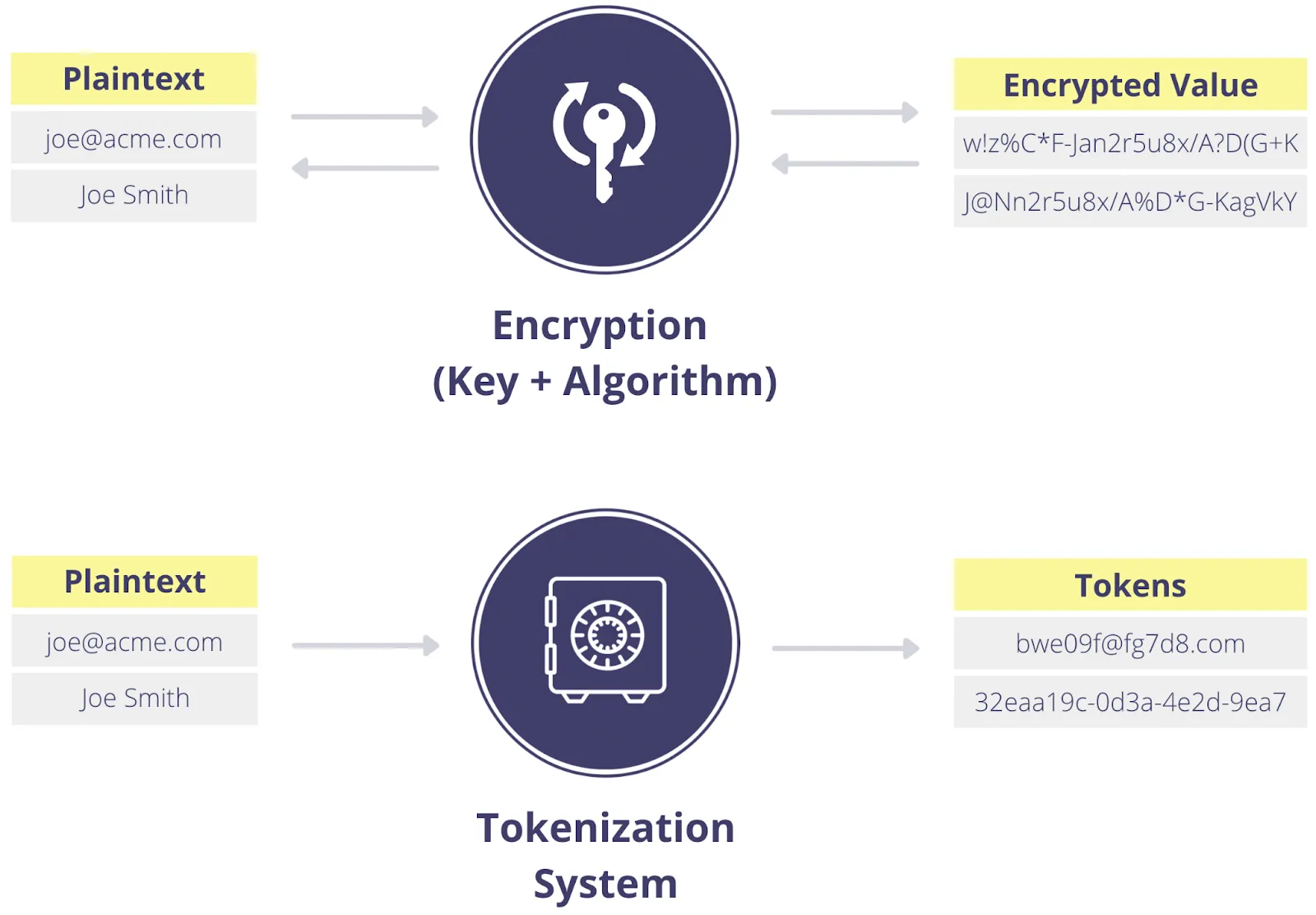
The Synergy: How Encryption and Advanced Tokenization Complement Each Other
Skyflow supports both encryption and tokenization as part of its data privacy vault solution, and these technologies work together to provide comprehensive protection for sensitive data. This layered approach moves beyond basic protection to meet the full security mandate of Rule 6.
- Tokenization Isolates Sensitive Data: Tokenization is a core capability that allows you to swap sensitive data for tokens (pseudorandom values without exploitable value) that can be safely stored in your operational databases and systems. Your applications work exclusively with these tokens, ensuring that sensitive data doesn't exist in your systems. Skyflow offers flexible tokenization options, including format-preserving tokens (that look like the original data) and the ability to use deterministic tokens for matching and joining data. For more information on tokenization specifically, check out Demystifying Tokenization: What Every Engineer Should Know.
- Encryption Secures Data within the Vault: When sensitive data is collected, it is securely stored in Skyflow’s Data Privacy Vault and is encrypted. The vault employs strong encryption, including proprietary polymorphic encryption techniques, to secure sensitive data while ensuring it remains usable.
The Dual-Layer Protection:
In Skyflow’s architecture, tokenization and encryption are fundamentally complementary. This process works as follows:
- When sensitive data is collected and centralized, it is immediately encrypted within the secure vault.
- Tokens are simultaneously generated and returned to your application to be used in place of the sensitive data.
- When the original data is genuinely needed, the token can be securely exchanged for the actual data through a controlled process.
This dual approach provides multiple layers of protection: encryption secures the data within the vault, while tokenization ensures that sensitive data doesn't exist in your operational systems. By centralizing all security functions from advanced tokenization and polymorphic encryption to access controls and auditing, Skyflow enables Data Fiduciaries to meet the detailed security mandates of DPDP Rule 6 without the complexity and risk associated with custom solutions. Utilizing both technologies helps minimize security risks by isolating sensitive data and reduces compliance burden.
Here is a high level look at Encryption vs Tokenization:
Advanced Tokenization: The Next Level of Data Protection
Rule 6 also permits the use of "virtual tokens mapped to that personal data" as a security safeguard. While traditional tokenization is often reversible, the concept of Irreversible Tokenization represents the most advanced standard of data privacy and security.
Skyflow’s Advanced Tokenization described in the previous section is really Irreversible Tokenization, a security method that substitutes sensitive information with unique, non-reversible tokens, thus achieving data anonymization that is impossible to reconstruct. This technique is distinct from reversible methods because it permanently severs any link to the original data, prioritizing maximum privacy and facilitating compliance with global standards.
Irreversible tokenization involves replacing sensitive data with unique, non-reversible tokens. This is highly significant for Rule 6 compliance because:
- Anonymization and De-linking: The process severs any link to the original data, ensuring unmatched privacy and security because the tokens cannot be reconstructed. This is particularly valuable for uses where the data should be fully anonymized to meet global standards.
- Secure Deletion: When irreversible data destruction or erasure is required (for example, when a Data Principal exercises their right to erasure under the Act, Skyflow ensures that tokenization and secure deletion occur together, leaving no retrievable trace of the original data.
- Compliance Support: While achieving true irreversibility, Skyflow’s data vault architecture still provides the necessary governance controls for managing sensitive data access and enables compliant re-identification when needed.
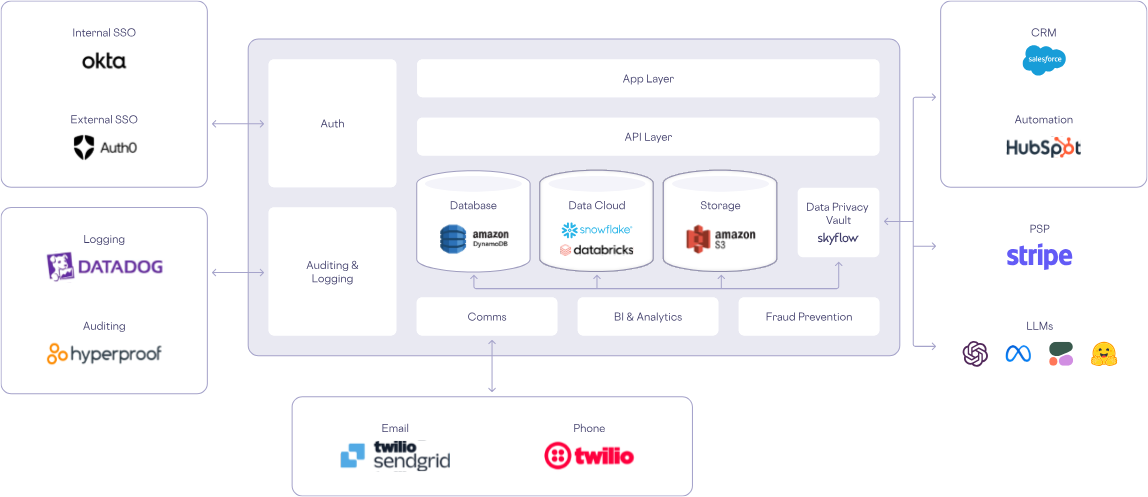
Tokenize sensitive data with Skyflow Data Privacy Vault to ensure data security across enterprise applications and third-party integrations.
Scale and Trust: A Proven Platform
This architectural choice is validated by its proven ability to handle substantial enterprise and global demands.
Skyflow’s Data Privacy Vault architecture is trusted by 3 Fortune 500 organizations and currently provides continuous protection for the personal data of over 1.5 billion customers across 28 countries. This massive operational volume - handling over 1.35 crore API calls every day - demonstrates that the Data Privacy Vault is a mature, scalable infrastructure that can genuinely deliver the requirements while meeting the performance and compliance requirements of the DPDP Act and other global regulations.
Bottom line: Meeting Rule 6 by Design, Architecture and the Right Technology
If there is one main take away here, it is that instead of building a fragmented system that attempts to retrofit security controls onto existing databases, the Data Privacy Vault architecture (followed by companies like Apple and Google) isolates the personal data separate from existing systems. This design, combined with the encryption and irreversible tokenization, inherently de-risks existing applications and analytical systems, providing a comprehensive solution for Rule 6. Here is a quick summary:
By centralizing all personal data security functions, from irreversible tokenization and polymorphic encryption with referential integrity to access controls and auditing, Skyflow enables DFs to meet the detailed security mandates of DPDP Rule 6 without the complexity and risk associated with custom-built or DIY solutions.
By ensuring that encryption and irreversible tokenization together with secure deletion happen simultaneously, Skyflow provides a seamless solution for privacy-first operations while also offering validation that meets DPDP Act compliance standards for de-identification, balancing strong security with necessary data utility.